Table of Contents
- Getting Started
- Agent-Based Monitoring
- Data Providers
- Directory Services
- Auditing
- Hosts
- Templates
- Template Properties
- Batch Update Templates
- Log Management Templates
- File and Directory Monitor Templates
- Windows Monitor Templates
- Account Lockout Monitor Template
- Logon Monitor Template
- CPU Monitor Template
- Memory Monitor Template
- Disk Space Monitor Template
- SMART Monitor Template
- Windows Update Template
- Process Monitor Template
- Service Monitor Template
- Performance Counter Monitor Template
- PowerShell Template
- Registry Value Monitor Template
- Active Directory User Monitor Template
- Active Directory User Integrity Monitor Template
- Task Scheduler Template
- Clock Synchronization Template
- Defragment NTFS Disks Template
- Network and Application Monitor Templates
- Database Monitor Template
- Directory Service Monitor Template
- DNS Blacklist Monitor Template
- DNS Monitor Template
- Domain Expiration Monitor Template
- Network Speed Monitor Template
- Ping Monitor Template
- Database Table Reseed
- SQL Server Shrink and Backup Template
- SSH Shell
- TCP Port Scan Monitor Template
- Website Monitor Template
- SSL Certificate Monitor Templates
- Email Monitor Templates
- SNMP Monitor Templates
- Monitors
- Reports
- Auto-Configurators
- Filters
- Actions
- Desktop Actions
- Email Actions
- Event Log Actions
- Executable Actions
- File Actions
- IIS IP Address Restriction Actions
- Microsoft Teams Actions
- PowerShell Actions
- Report Actions
- Service Actions
- SMS Actions
- SNMP Trap Actions
- Syslog Actions
- Template Actions
- IIS IP Address Restriction Actions
- Action Variables
- Schedules
- Environment Variables
- Options
- Account Lockout Monitoring and Reporting
- Merging Logs
- SNMP
- SSH Shell
- Syslog
- Exporting and Importing Configuration Objects
- Shared Views
- Auto-Config Host Assignment Properties
- General Executable Properties
- Assign Actions
- Assign Directories
- Assign Disks
- Assign Shares
- Assign Files
- Assign Consolidated Logs
- Assign Event Logs
- Assign Azure Audit Logs
- Target Files and Sub-Directories
- Define Log Entry Columns
- Define Log Entry Columns with Regular Expressions
- Define CSV and W3C Log Entry Columns
- Active Directory User and Group Filters
- Explicitly Assigned Logs
- File Explorer
- Report Columns
- Report Date/Time Ranges
- Report Security Event Log Filters
- Select Folder or File
- Executable Timeline
- Command Line Interface
- Troubleshooting
- Terminology
Corner Bowl Server Manager
SIEM, IPS, Server Monitoring, Uptime Monitoring and Compliance Software
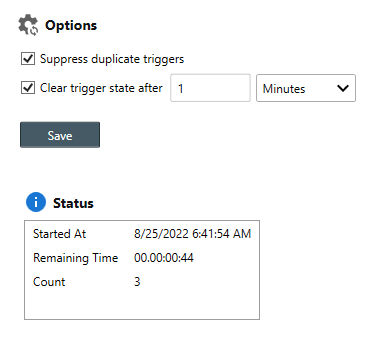
Monitor Action Suppression Properties
When monitoring endpoints that can trigger a high frequency of actions (e.g. Ping and CPU Monitors), it may become necessary to temporarily suppress, pause or silence the monitors so actions are dropped for a period of time (e.g. When applying operating system patches or making DNS changes).
Use the Action Suppression Tab found within the Monitor Status View to temporarily suppress monitor actions.
How to temporarily suppress monitor actions:
- From the Explorer View, navigate to the host that is triggering actions then expand.
- Find the assigned Template, also known as a Monitor, then right click and select Explore. The Monitor Status View displays.
- From the Monitor Status View, select the Action Suppression Tab.
- Use the Suppress duplicate triggers option to suppress duplicate actions from being re-run after a monitor re-triggers or re-errors (e.g. If running a Ping Monitor every 15 seconds, you will no longer receive subsequent notifications the first alert. Subsequent alerts will only be sent after the triggered state is cleared).
- Use the Re-enable after option to automatically re-enable actions after the defined frequency (e.g. If this value is set to re-enable after 15 minutes, all actions are suppressed for 15 minutes). Once automatically re-enabled, the assigned actions will run the next time the monitor triggers.
-
Once enabled, the Status Table displays the following metadata:
Attribute Value Started At The time monitor actions was temporarily suppressed. Remaining The amount of remaining time before the monitor can trigger actions again. Count The number of suppressed actions.
 |
Monitor action suppression settings are saved to memory only. Restarting the service clears all previously set monitor action suppression settings. |