Table of Contents
- Getting Started
- Agent-Based Monitoring
- Data Providers
- Directory Services
- Auditing
- Hosts
- Templates
- Template Properties
- Batch Update Templates
- Log Management Templates
- File and Directory Monitor Templates
- Windows Monitor Templates
- Account Lockout Monitor Template
- Logon Monitor Template
- CPU Monitor Template
- Memory Monitor Template
- Disk Space Monitor Template
- SMART Monitor Template
- Windows Update Template
- Process Monitor Template
- Service Monitor Template
- Performance Counter Monitor Template
- PowerShell Template
- Registry Value Monitor Template
- Active Directory User Monitor Template
- Active Directory User Integrity Monitor Template
- Task Scheduler Template
- Clock Synchronization Template
- Defragment NTFS Disks Template
- Network and Application Monitor Templates
- Database Monitor Template
- Directory Service Monitor Template
- DNS Blacklist Monitor Template
- DNS Monitor Template
- Domain Expiration Monitor Template
- Network Speed Monitor Template
- Ping Monitor Template
- Database Table Reseed
- SQL Server Shrink and Backup Template
- SSH Shell
- TCP Port Scan Monitor Template
- Website Monitor Template
- SSL Certificate Monitor Templates
- Email Monitor Templates
- SNMP Monitor Templates
- Monitors
- Reports
- Auto-Configurators
- Filters
- Actions
- Desktop Actions
- Email Actions
- Event Log Actions
- Executable Actions
- File Actions
- IIS IP Address Restriction Actions
- Microsoft Teams Actions
- PowerShell Actions
- Report Actions
- Service Actions
- SMS Actions
- SNMP Trap Actions
- Syslog Actions
- Template Actions
- IIS IP Address Restriction Actions
- Action Variables
- Schedules
- Environment Variables
- Options
- Account Lockout Monitoring and Reporting
- Merging Logs
- SNMP
- SSH Shell
- Syslog
- Exporting and Importing Configuration Objects
- Shared Views
- Auto-Config Host Assignment Properties
- General Executable Properties
- Assign Actions
- Assign Directories
- Assign Disks
- Assign Shares
- Assign Files
- Assign Consolidated Logs
- Assign Event Logs
- Assign Azure Audit Logs
- Target Files and Sub-Directories
- Define Log Entry Columns
- Define Log Entry Columns with Regular Expressions
- Define CSV and W3C Log Entry Columns
- Active Directory User and Group Filters
- Explicitly Assigned Logs
- File Explorer
- Report Columns
- Report Date/Time Ranges
- Report Security Event Log Filters
- Select Folder or File
- Executable Timeline
- Command Line Interface
- Troubleshooting
- Terminology
Corner Bowl Server Manager
SIEM, IPS, Server Monitoring, Uptime Monitoring and Compliance Software
Duplicate Files Reports
The Duplicate Files Reports enable you to either manually on-demand scan any disk or directory then, using your own criteria, generate a report a report that lists duplicate files and optionally schedule the to be emailed to you or output to a file, for example, a CSV file.
Requirements
| Operating System | Technology |
|---|---|
| Windows | Remote WMI and Windows Shares |
| Linux | SFTP/SSH or FTP/S |
How to create a Duplicate Files Report:
- From the Menu Bar select File | New. The Create New Object View displays.
-
From the Create New Object View, expand Report | File and Permissions Reports then select Duplicate Files Report. The Properties View displays.

Unlicensed report types appear in gray text. If you would like to create a report that is not currently licensed, please contact Corner Bowl Software to upgrade your license. - The Properties View contains 6 configuration tabs.
How to configure the Duplicate Files Report
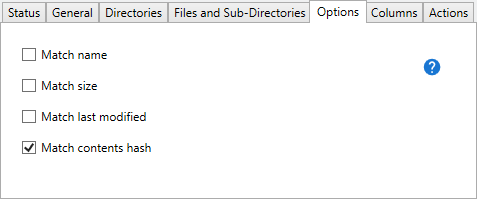
- Use the Match name check box to define a duplicate file when the names are the same.
- Use the Match size check box to define a duplicate file when the file sizes are the same.
- Use the Match last modified check box to define a duplicate file when the last modified date and times are the same.
- Use the Match contents hash check box to scan each file, generate a hash based on the file contents, then define duplicate files when the content hashes are the same.