Table of Contents
- Getting Started
- Agent-Based Monitoring
- Data Providers
- Directory Services
- Auditing
- Hosts
- Templates
- Template Properties
- Batch Update Templates
- Log Management Templates
- File and Directory Monitor Templates
- Windows Monitor Templates
- Account Lockout Monitor Template
- Logon Monitor Template
- CPU Monitor Template
- Memory Monitor Template
- Disk Space Monitor Template
- SMART Monitor Template
- Windows Update Template
- Process Monitor Template
- Service Monitor Template
- Performance Counter Monitor Template
- PowerShell Template
- Registry Value Monitor Template
- Active Directory User Monitor Template
- Active Directory User Integrity Monitor Template
- Task Scheduler Template
- Clock Synchronization Template
- Defragment NTFS Disks Template
- Network and Application Monitor Templates
- Database Monitor Template
- Directory Service Monitor Template
- DNS Blacklist Monitor Template
- DNS Monitor Template
- Domain Expiration Monitor Template
- Network Speed Monitor Template
- Ping Monitor Template
- Database Table Reseed
- SQL Server Shrink and Backup Template
- SSH Shell
- TCP Port Scan Monitor Template
- Website Monitor Template
- SSL Certificate Monitor Templates
- Email Monitor Templates
- SNMP Monitor Templates
- Monitors
- Reports
- Auto-Configurators
- Filters
- Actions
- Desktop Actions
- Email Actions
- Event Log Actions
- Executable Actions
- File Actions
- IIS IP Address Restriction Actions
- Microsoft Teams Actions
- PowerShell Actions
- Report Actions
- Service Actions
- SMS Actions
- SNMP Trap Actions
- Syslog Actions
- Template Actions
- IIS IP Address Restriction Actions
- Action Variables
- Schedules
- Environment Variables
- Options
- Account Lockout Monitoring and Reporting
- Merging Logs
- SNMP
- SSH Shell
- Syslog
- Exporting and Importing Configuration Objects
- Shared Views
- Auto-Config Host Assignment Properties
- General Executable Properties
- Assign Actions
- Assign Directories
- Assign Disks
- Assign Shares
- Assign Files
- Assign Consolidated Logs
- Assign Event Logs
- Assign Azure Audit Logs
- Target Files and Sub-Directories
- Define Log Entry Columns
- Define Log Entry Columns with Regular Expressions
- Define CSV and W3C Log Entry Columns
- Active Directory User and Group Filters
- Explicitly Assigned Logs
- File Explorer
- Report Columns
- Report Date/Time Ranges
- Report Security Event Log Filters
- Select Folder or File
- Executable Timeline
- Command Line Interface
- Troubleshooting
- Terminology
Corner Bowl Server Manager
SIEM, IPS, Server Monitoring, Uptime Monitoring and Compliance Software
Event Log Monitor Template
Event Log Monitoring is the process of subscribing too or polling Windows Event Log Entries, filtering entries, then, executing notification and remediation actions. The Event Log Monitor Template is used by network administrators and security compliance auditors that want to pro-actively monitor their network infrastructure and Security Event Logs for un-authorized activity.
In this Topic
- Event Log Monitoring Methods
- How to create an Event Log Monitor
- How to enable Real-Time Event Log Monitoring
- How to use the Corner Bowl Server Manager Agent instead of WMI
Event Log Monitoring Methods
Server Manager offers several different methods to monitor Windows Event Logs.
| Method | Agent-Based | Is Security Threat | Description |
|---|---|---|---|
| Remote WMI Event Subscriptions | No | Yes Source | Supported out-of-the-box on all versions of Windows. |
| Remote WMI Queries | No | Yes Source | Supported out-of-the-box on all versions of Windows. |
| Local WMI Event Subscriptions | Yes | No | Using our Agent Service, the Agent opens a persistent connection to the Management Server, locally subscribes to Event Logs through local WMI, then when an entry is received, applies filters then sends each entry that passes to the Management Server to execute notifications and remediation actions. |
| Local WMI Queries | Yes | No | Using our Agent Service, the Agent connects to the Management Server at a configured frequency, connects to the Event Log through local WMI, filters entries, then passes all filtered entries to the Management Server in a batch to execute notifications and remediation actions. |
How to create an Event Log Monitor
- From the Menu Bar, select File | New. The Create New Object View displays.
- From the Create New Object View, expand Templates | Log Management and finally select Log Monitor. The New Template View displays.
- The Template Properties View contains 7 tabs.
How to enable Real-Time Event Log Monitoring
- Select the General Tab
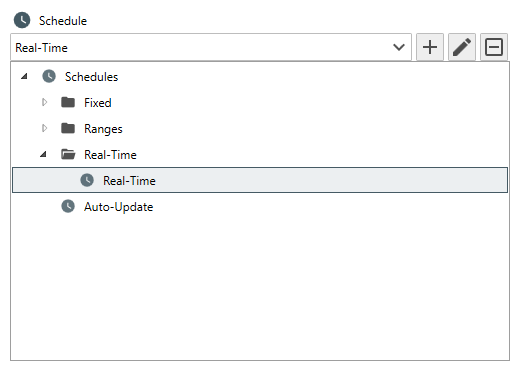
- From the Schedule Drop-Down, expand the Real-Time Group then select Real-Time.
- Select the Options Tab
-
When configuring a Microsoft Application Log, check the Enable WMI API checkbox.

When this option is set, several required Windows Registry entries are added to the managed host prior to downloading. - Use the Assignments View to assign the target hosts or groups of hosts.
- Click the Save button, then, if you want to use the Agent instead of remote WMI, from the Object Explorer, find the target server or group of servers, right click, then select Host Properties. The Host Properties View displays.
-
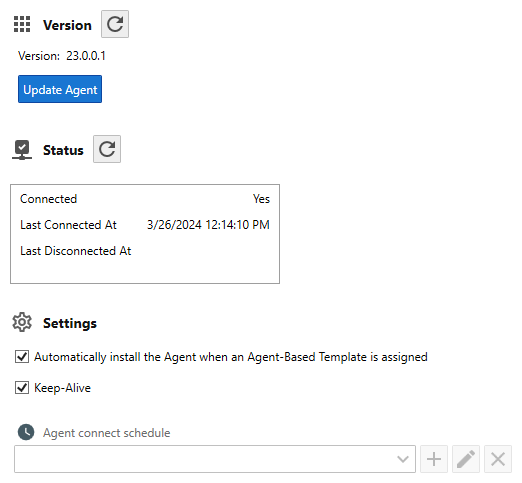
From the Host Properties View, select the General Tab, scroll down until you see the Agent Settings group.
First, verify the Agent version is listed. If not, RDP into the remote server, verify the Corner Bowl Server Manager Agent is installed then locate the agent.log file.
Take a look at the end of the log file for detailed information on the connection status. Often the issue is related to:
- A mis-configured hostname in the tcpserver.json
- A DNS name resolution issue
- A rolling IP on the Management Server
- A firewall blocking port 21843, or, on the server-side, the configured Host Identification Method.
- Once the installed version is verified, check the Keep agent connected Checkbox then click the Save Button to save your changes.

Once saved, each assigned Agent will automatically start the Real-Time Event Log Monitor the next time it connects to the Management Server.
How to use the Corner Bowl Server Manager Agent instead of Remote WMI (DCOM)
- Select the Agent Template Tab
- Check the Enabled Checkbox