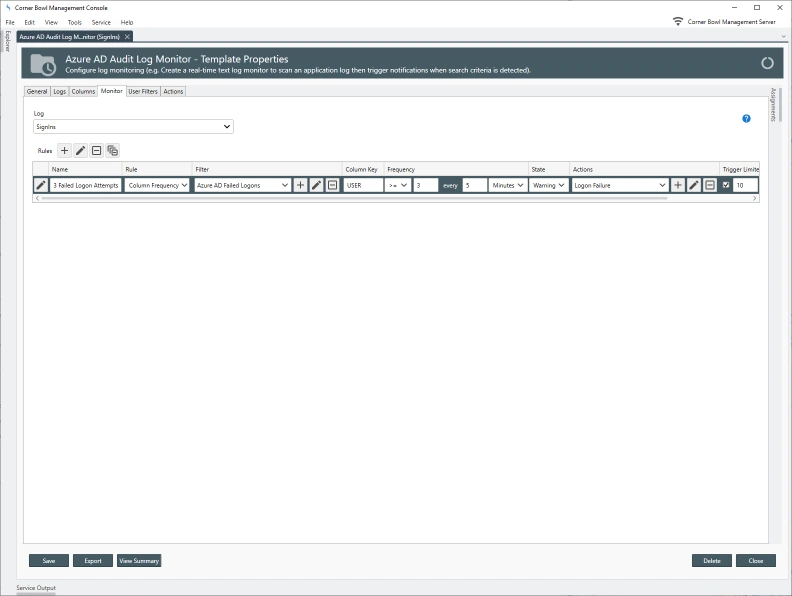
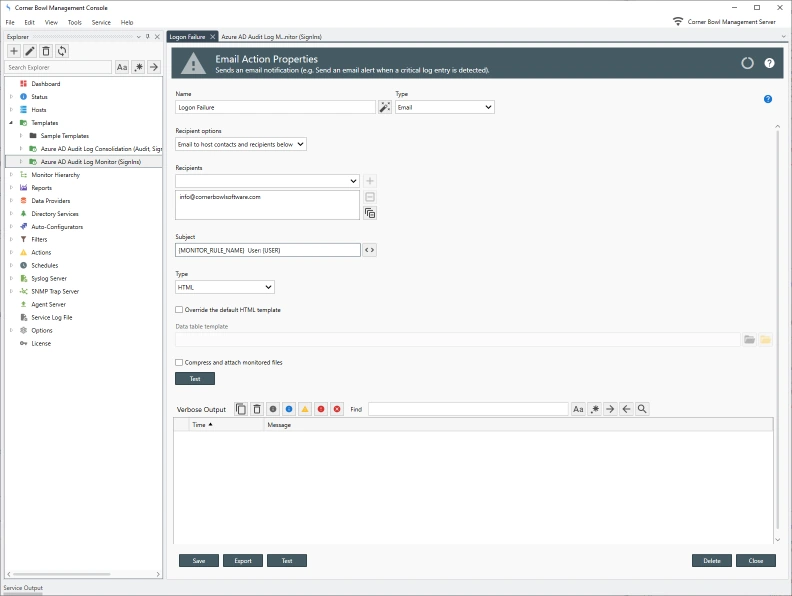
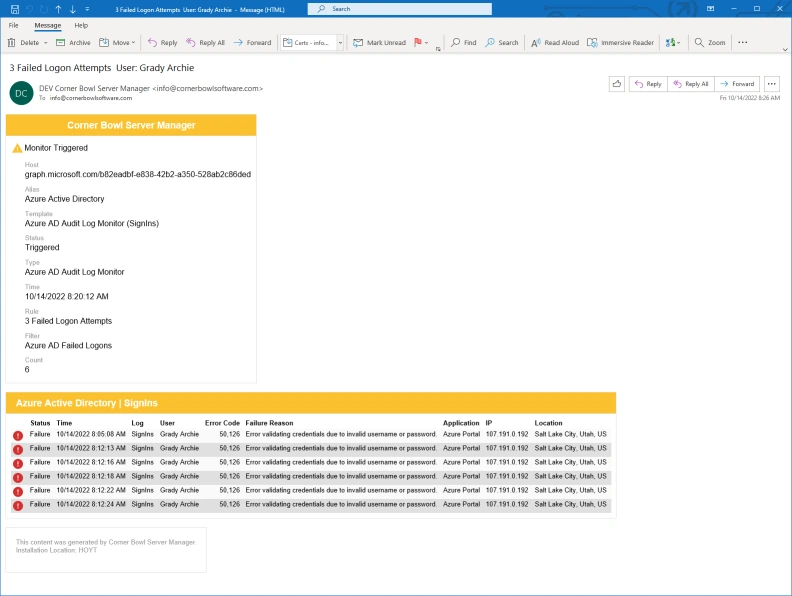
How to Configure your Azure Portal for Remote Access
Before Server Manager can monitor Azure Active Directory Audit Logs the target Azure Portal must be configured to allow the log entries to be downloaded by Server Manager.
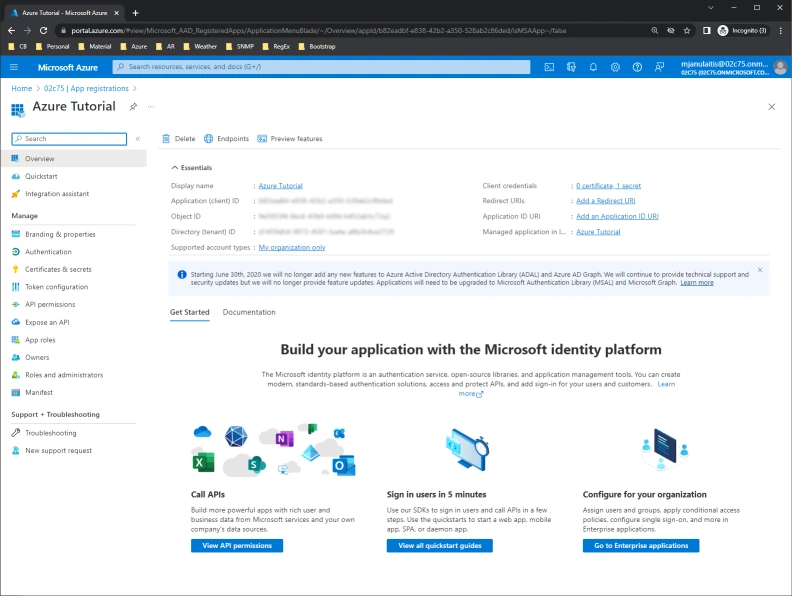
- Open your Internet Browser then navigate to portal.azure.com.
- Once logged in, select Azure Active Directory.
- Next, click App registrations, then New registration.
- Specify a friendly name then click Register. The App Registration Overview displays.
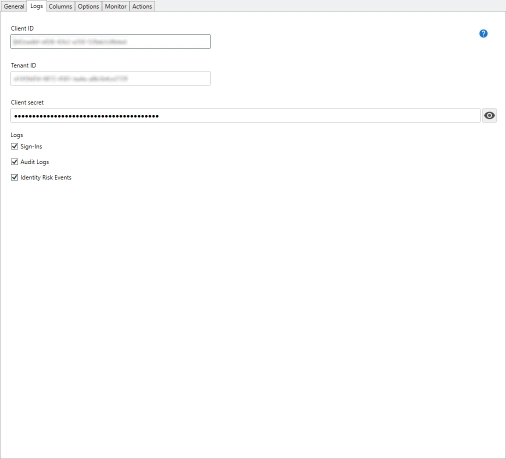
- Copy the Application (client) ID and Directory (tenant) ID then paste to a text editor for later use.
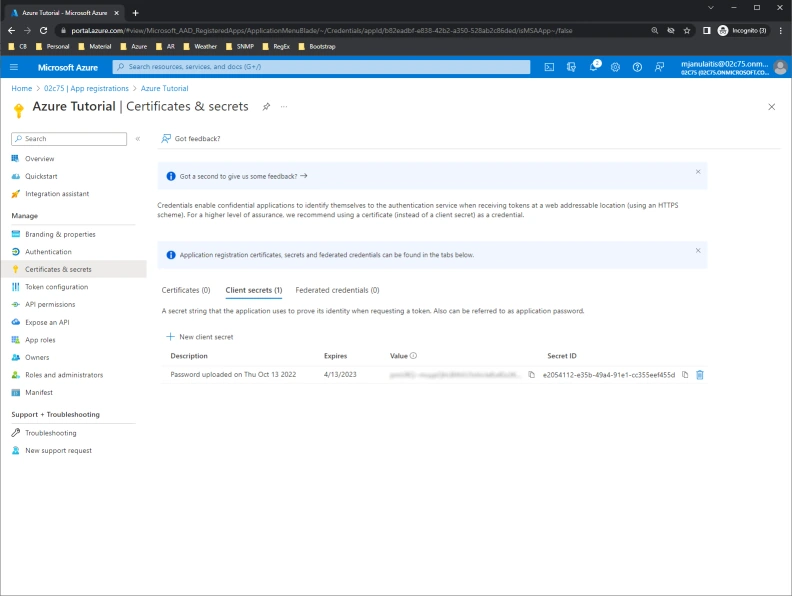
- Next, click Certificates and secrets, then New Client Secret, then Add. Copy the secret then paste to a text editor for later use.
-
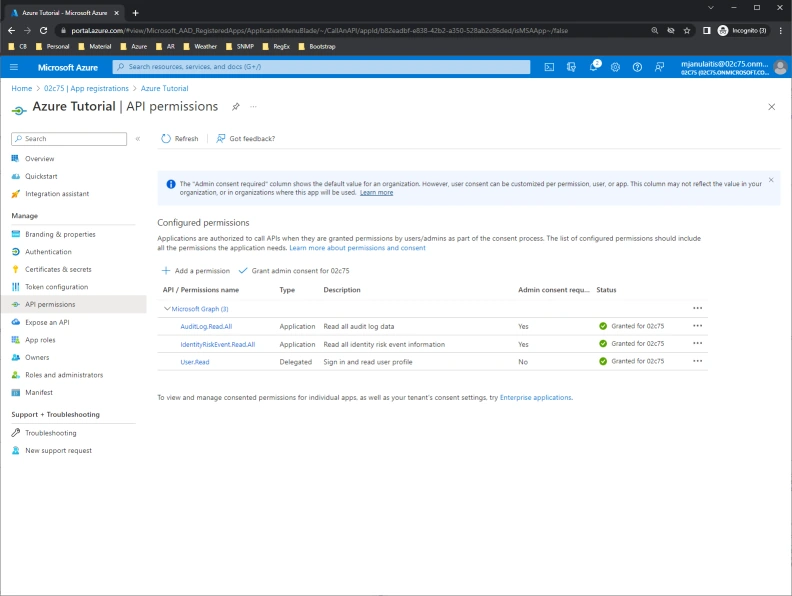
Next, click API permissions. Grant the following additional Microsoft Graph/Application permissions:
- AuditLog.Read.All
- IdentityRiskEvent.Read.All
- Finally, click Grant admin consent.
 button to automatically update the template name.
button to automatically update the template name.
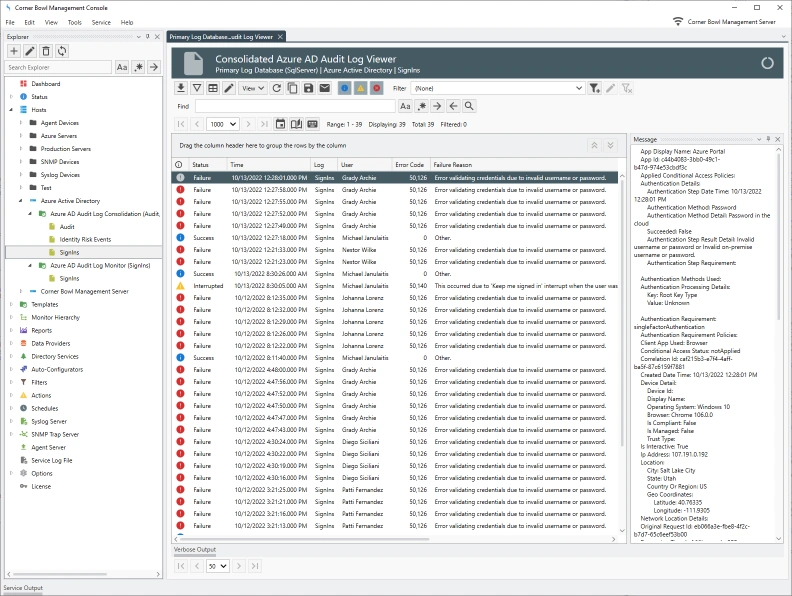
 button. The Select Log View Options Dialog displays. Leave the defaults then click OK. The Consolidated Azure AD Audit Log View displays.
button. The Select Log View Options Dialog displays. Leave the defaults then click OK. The Consolidated Azure AD Audit Log View displays.
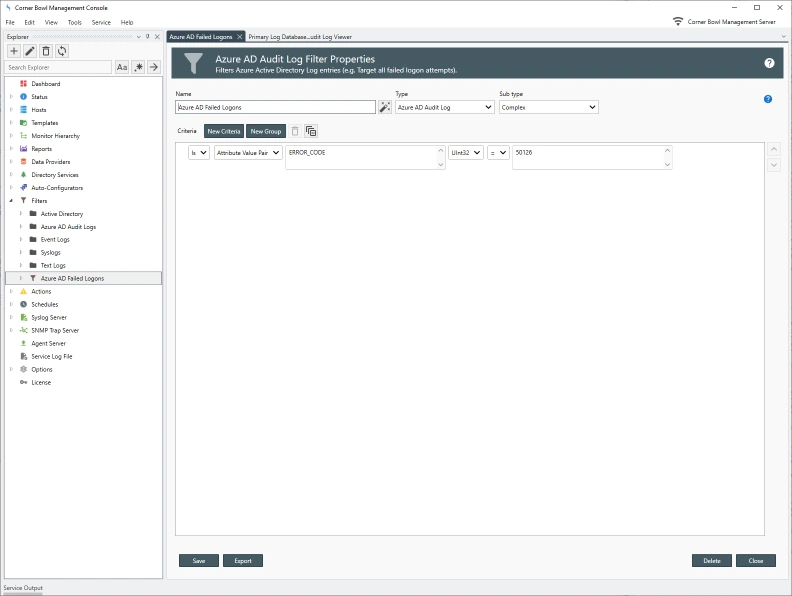
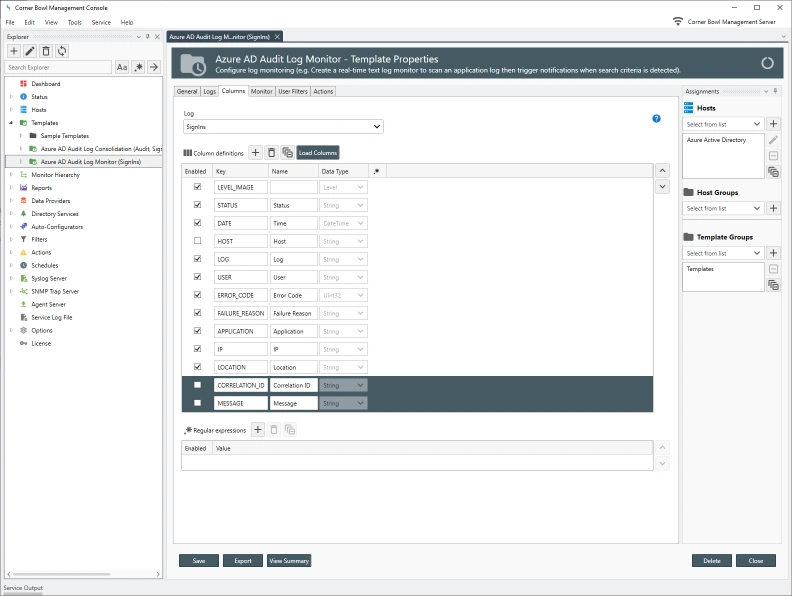
 button. A new line item is added.
button. A new line item is added.