SIEM, Vulnerability Scanning, Server Monitoring and Compliance Training
Cost-effective security software and compliance training with unmatched support
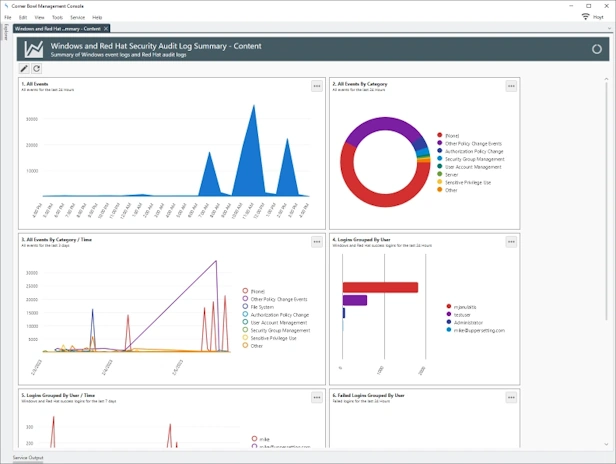
Security Information and Event Management
SIEM | Log Collection | Log Retention | Log Monitoring
Manage Azure, Windows, Linux, Red Hat, CentOS, Ubuntu and network hardware logs. Agent-based and agentless options for Windows and Linux. Batch Import and Audit Windows Event Log Files for CMMC and JSIG Compliance.
Compliance
CMMC | NIST | JSIG | CJIS | PCI/DSS | GDPR | ISO 27001
Out-of-the-box compliance controls, over 100 built-in security audit reports and a built-in audit tracking system to prove compliance to your auditors.
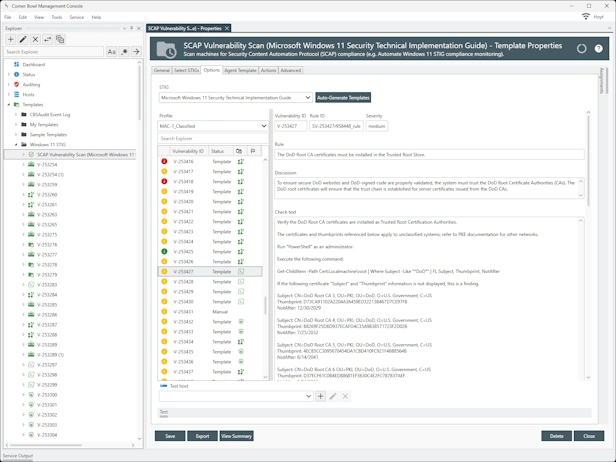
SCAP Vulnerability Scanner | Compliance Checker
Automate Vulnerability and Compliance Scanning
Automate SCAP compliance checking and vulnerability scanning, generate DISA STIG Viewer checklist files and view STIG differences when new versions are released.
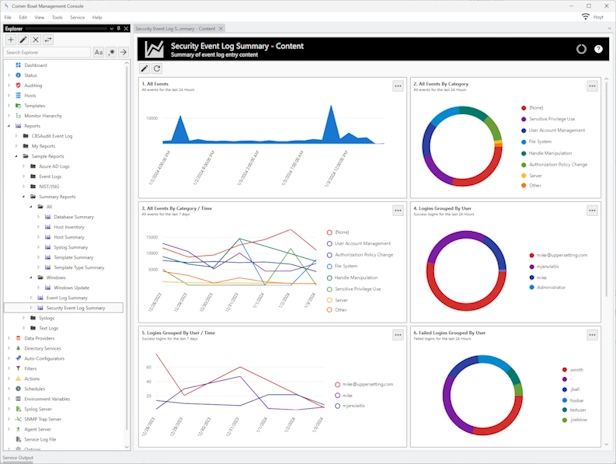
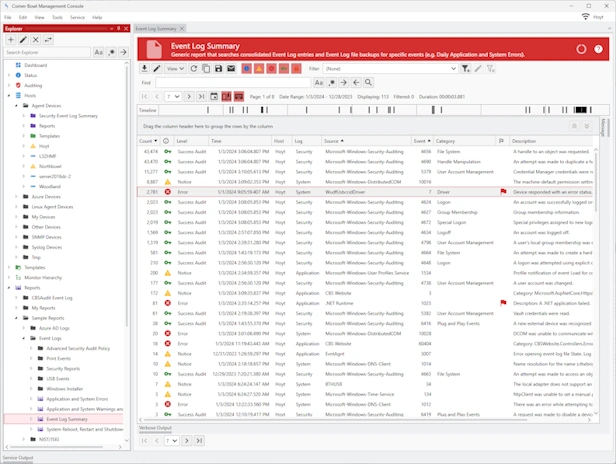
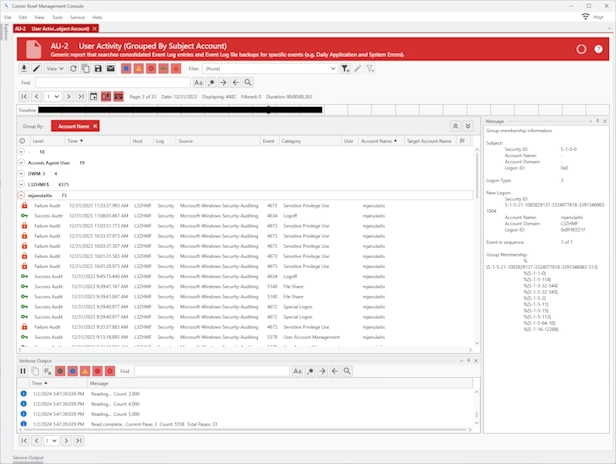
Event Log Management
Event Log Consolidation | Event Log Monitoring | Event Log Analyzer
Agent-based and agentless event log consolidation, backups, archiving, retention, parsing, real-time monitoring and security audit reporting.
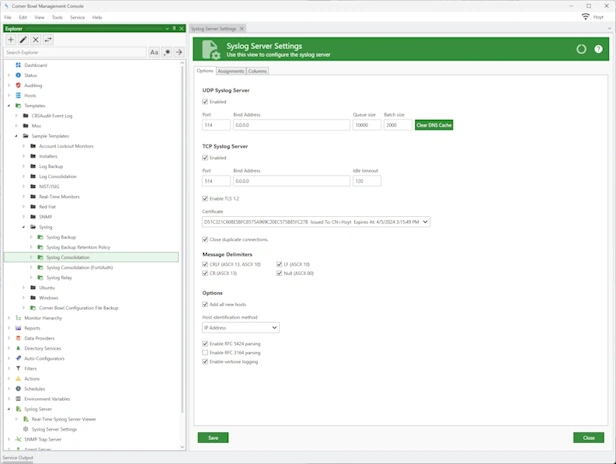
Syslog Server
Syslog Consolidation | Syslog Monitoring | Syslog Analyzer
Centrally manage all of your hardware devices with our high throughput UDP and TCP Red Hat, CentOS, Ubuntu and Windows Syslog servers.
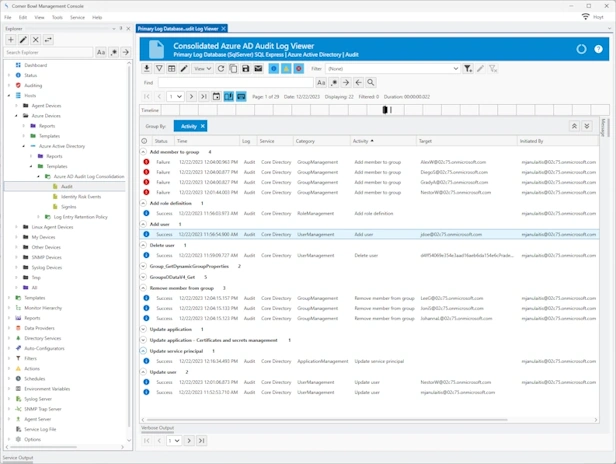
Microsoft Azure
Audit Log Management | Azure File Shares Monitoring
Cloud-based and on-premises Azure Microsoft Entra ID and Office 365 audit log, sign-in log and identity risk events log management. Azure File Share monitoring and analysis.
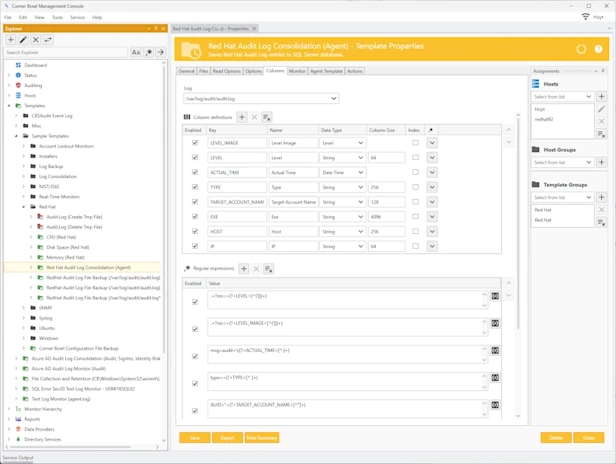
Linux, Red Hat, CentOS and Ubuntu Audit Log Management
Linux Log Consolidation | Linux Log Monitoring | Linux Log Analyzer
Agent-based Linux, Red Hat Enterprise Linux, CentOS and Ubuntu log management to meet all of your compliance and auditing requirements.
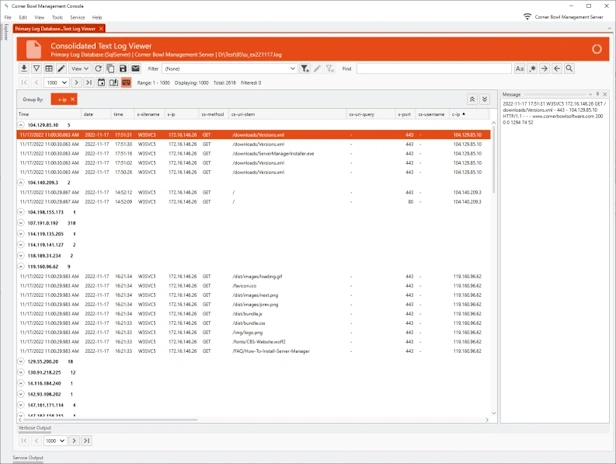
Text Log Management
Text Log Management | Text Log Monitoring | Text Log Analyzer
Centrally consolidate, backup, archive, retain, parse, monitor and analyze W3C, CSV, IIS Logs, Windows firewall logs and any other text-base log file on both Windows and Linux.
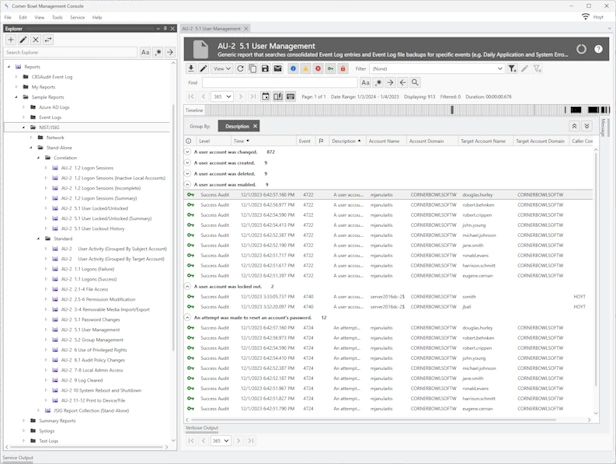
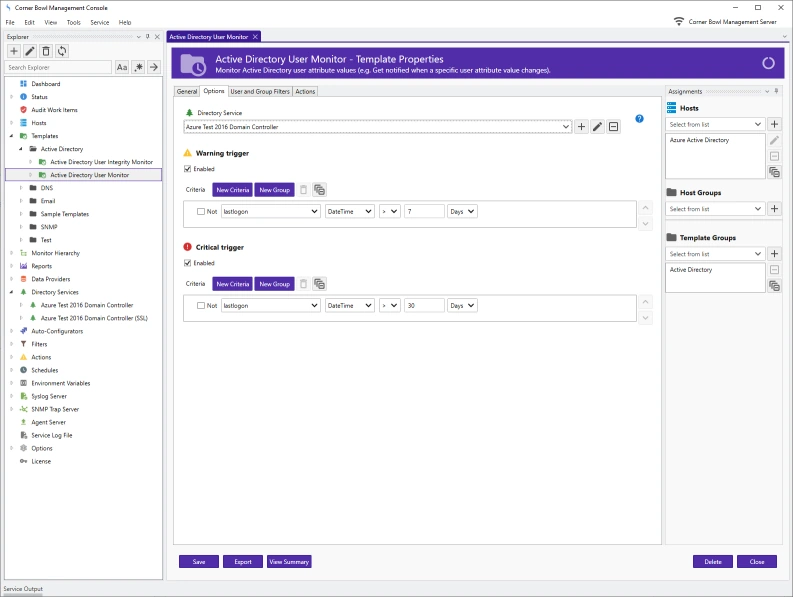
Active Directory, File and Account Auditing
AD | User Activity | Permissions | File Integrity Monitoring
Monitor Active Directory and Microsoft Entra ID changes, user activity, file access permissions, file integrity and Windows account integrity.
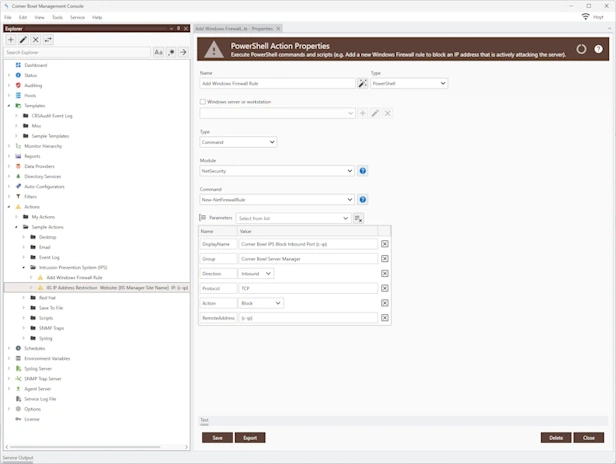
Threat Detection, Notification and Remediation
Intrusion Detection System (IDS) | Intrusion Prevention System (IPS)
Detect intrusions in real-time, notify and take meaningful action to automatically block active cyber-attacks and prevent new cyber-attacks.
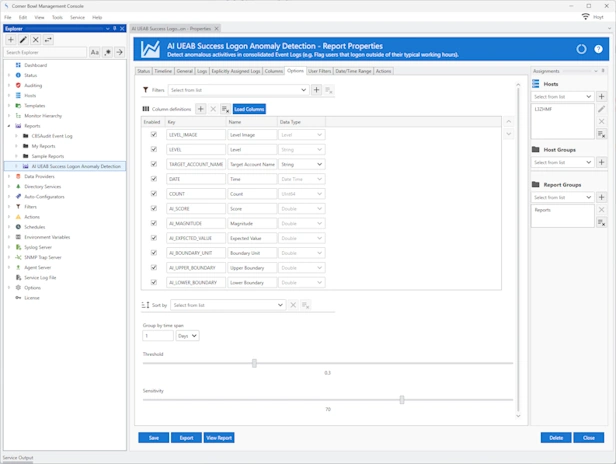
Artificial Intelligence | User Behavior Analytics
AI Generated UEBA Reports
Out-of-the-box User and Entity Behavior Analytics (UEBA) AI generated Security Reports to identify anomalous activity. Create, customize and generate your own reports to detect anomalous activity from any device's audit logs.
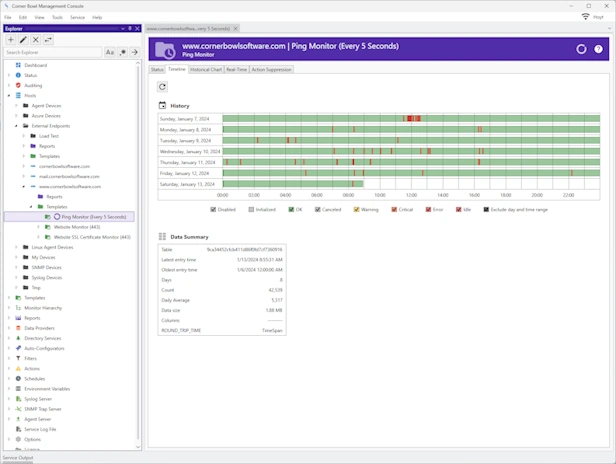
Network Monitoring
Ping | Network Speed | TCP Port Scanning
Built-in tools to monitor ICMP Ping response times, network packet transfer rates, and scan open TCP ports from managed systems to any endpoint.
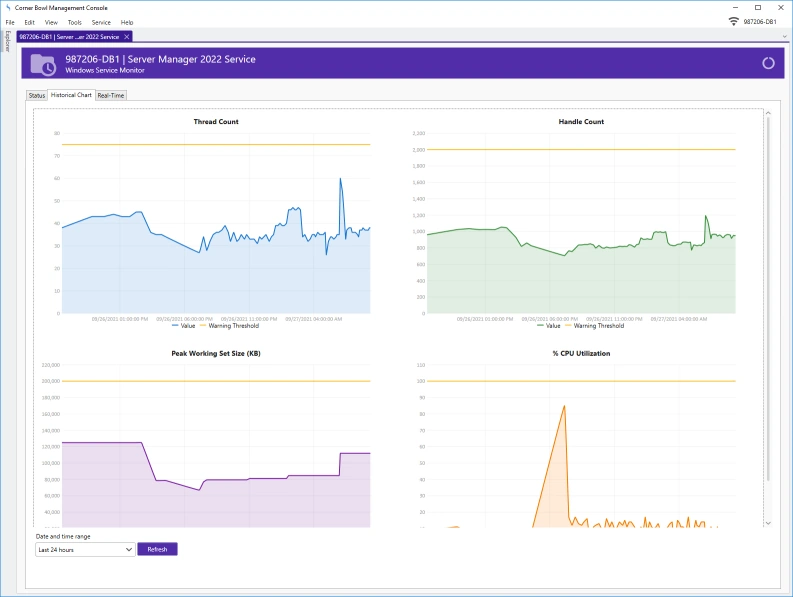
Server Monitoring
CPU | Memory | Disk Space | Services | Resources
Monitor critical system resources and applications on Windows and Linux Servers and Docker Containers.
Application Monitoring
Database | LDAP | Docker Containers
Monitor database performance, result sets, LDAP content, and Docker Container performance.
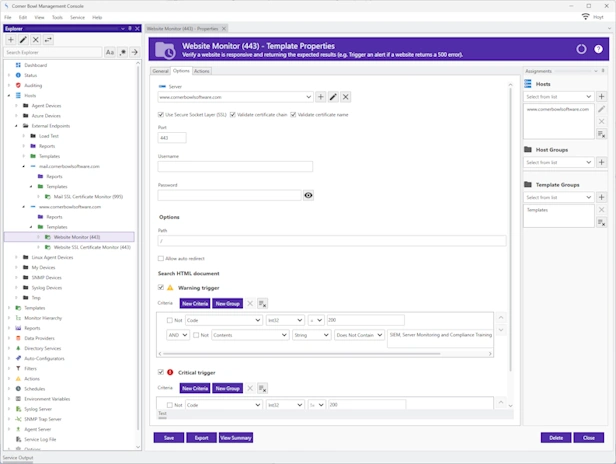
Website Monitoring
HTTPs | SSL Certificates | Email | DNS | FTP
Monitor website performance, content, SSL certificates, DNS records, blacklists and much more.
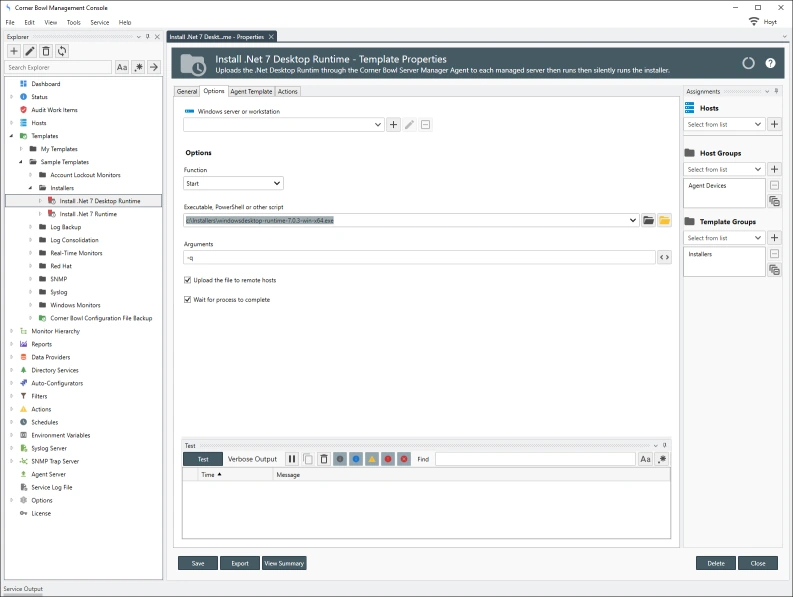
Automation
Automate | Deploy | Remote Execute
Schedule and automate tasks, PowerShell scripts and executables on any managed system.
BI Dashboard Integration
Power BI or any other BI Platform
Seamlessly integrate with any BI Dashboard Platform with our open history and log database schemas.
Testimonials
Last Updated: August 21st, 2025