What is Text Log Monitor?
Corner Bowl Text Log Monitor is an extensive enterprise-class SIEM software monitoring and management tool for IT professionals that includes centralized log consolidation to native format, SQL Server, MySQL or SQLite, real-time and scheduled text log monitoring and application log file monitoring, a powerful text log analyzer with paging support for large files, IIS, W3C and CSV file support, regular expression support, and more. Text Log Monitor will help you fulfill compliance requirements for CJIS, CMMC, JSIG, NIST, GDPR, HIPAA, PCI/DSS and SOX.
Monitor IIS, W3C, CSV and any Text-Based Application Log File
- IIS, W3C and CSV files are programmatically parsed, data types calculated and column definitions automatically created.
- Multi-line delimited files are read line by line until the next end-of-entry or entry delimiter is reached. Once reached, all lines are concatenated together to form the complete original entry. Users can define a wide range of entry delimiter criteria including date and time rules.
- Most common are non-delimited files. These files do not follow a pattern and are read and filtered one line at a time.
Monitor Rolling Log Files
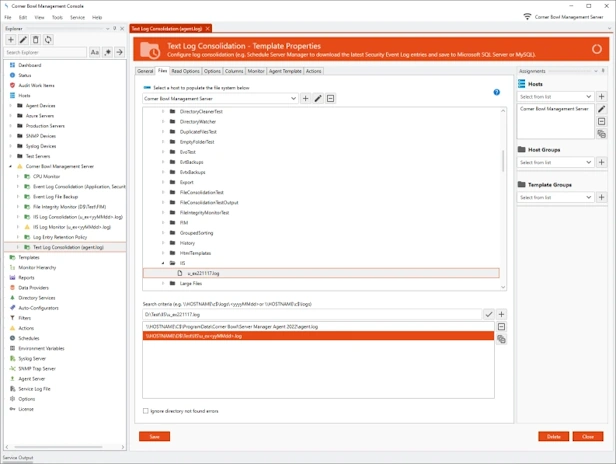
- Many applications create log files using a numeric or date driven naming mechanism. Text Log Monitor enables you to dynamically monitor these files using user defined filename search criteria which includes date and time based criteria (e.g. *.txt and u_ex<yyyyMMdd>.log).
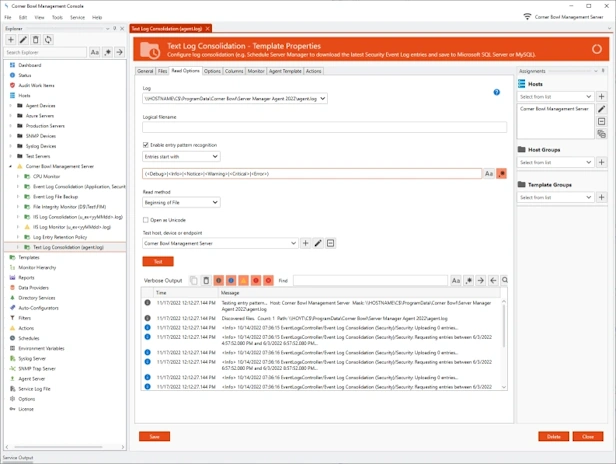
Text Log Consolidation
- Consolidate your log files by centrally saving and backing up your text and application log entries to either Microsoft SQL Server, MySQL or SQLite.
- Use regular expressions and our W3C/CSV parser to parse attribute value pairs to their native data types then save to your RDBMS for internal and external analysis (e.g. integer, decimal and date/time).
- Parse Linux Audit log files and extract attribute value pairs.
- Use our Log Entry Retention Policy Template to automatically delete old log entries no longer required for compliance.
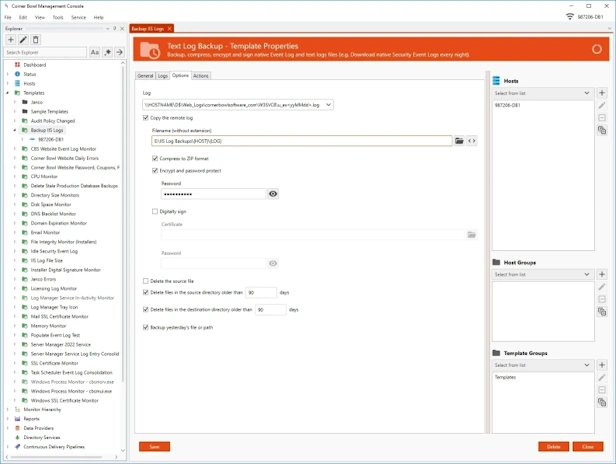
Text Log File Backup
- Centrally save, backup, zip, encrypt and digitally sign text and application logs files in their native format.
- Use our Directory Cleaner Template to automatically delete old event log file backups no longer required for compliance.
Text Log Monitor
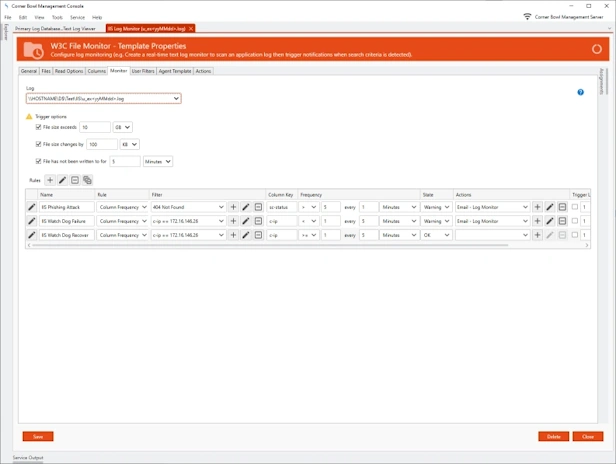
- Real-time monitor or schedule monitor any text-based application log file.
- Use regular expressions and our W3C/CSV parser to parse attribute value pairs to their native data types for use in filters (e.g. integer, decimal and date/time).
- Parse Linux Audit log files and extract attribute value pairs.
- Create Complex Filter Criteria with support for any data type.
- Apply frequency rules (e.g. Get notified when an error occurs 3 times within 5 minutes).
- Includes maintenance schedule rules.
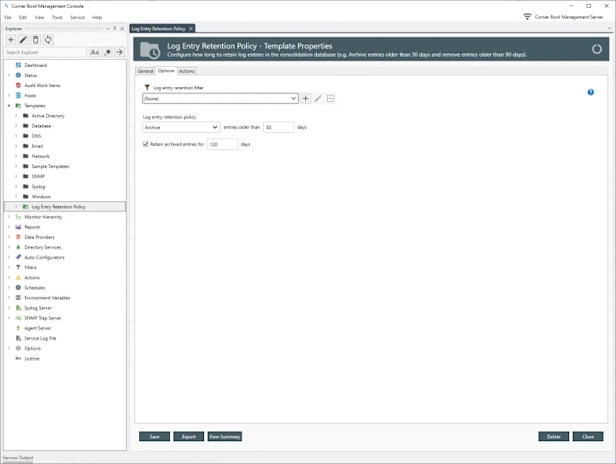
Text Log Entry Retention Policy
- Configure how long to retain text log entries in the log databases (e.g. Archive entries older than 30 days and remove entries older than 90 days).
- Schedule and manually remove text log entries no longer required for analysis and compliance.
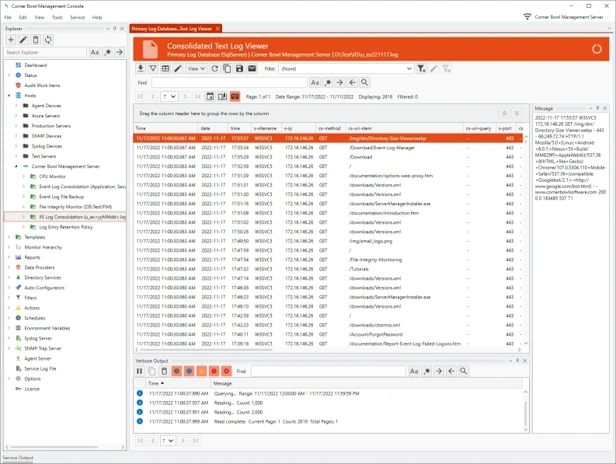
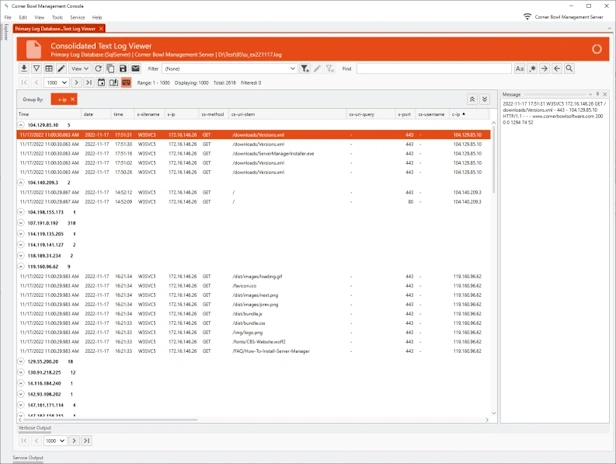
Text Log Analyzer
- Watch text logs in real-time.
- Page through large log files, search, highlight, view frequencies, mark entries and export result sets.
- Group and sort log entries using complex regular expression driven attribute value search criteria.
- Create complex filters from messages.
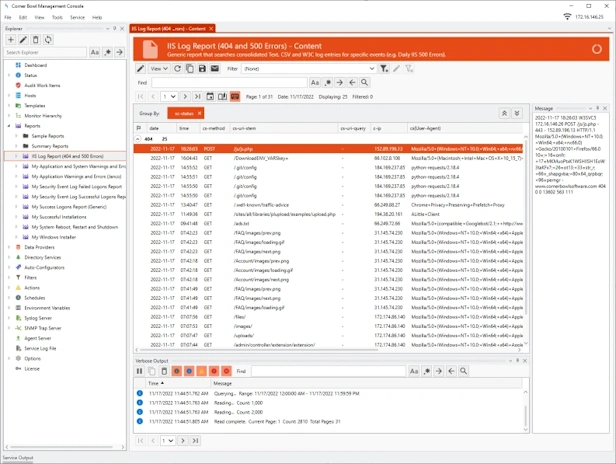
Schedule Analysis and Compliance Reports
- Schedule daily analysis reports that scan, filter, export and email specific consolidated text log entries.
- Run interactive compliance reports on-demand.