Table of Contents
- Getting Started
- Agent-Based Management
- Common Tasks
- Data Providers
- Directory Services
- Auditing
- Hosts
- Templates
- Template Properties
- Batch Update Templates
- Assign Templates
- Log Management Templates
- SCAP Compliance Monitor
- Active Directory User Monitor Templates
- File and Directory Monitor Templates
- Windows Monitor Templates
- CPU Monitor Template
- Memory Monitor Template
- Disk Space Monitor Template
- Account Lockout Monitor Template
- Audit Policy Monitor Template
- Logon As Monitor Template
- Logon Monitor Template
- Performance Counter Monitor Template
- PowerShell Template
- Process Monitor Template
- RDP Session Monitor Template
- Registry Value Monitor Template
- Service Monitor Template
- SMART Disk Monitor Template
- System Security Monitor Template
- Windows Update Template
- WMI Query Template
- Task Scheduler Template
- Clock Synchronization Template
- Defragment NTFS Disks Template
- Network and Application Monitor Templates
- SSL Certificate Monitor Templates
- Database Templates
- Email Monitor Templates
- SNMP Monitor Templates
- Windows Accounts Templates
- Monitors
- Reports
- Auto-Configurators
- Filters
- Actions
- Schedules
- Environment Variables
- Options
- SNMP
- SSH Shell
- Syslog
- System Reset
- Shared Views
- Active Directory User and Group Filters
- Assign Actions
- Assign Azure Audit Logs
- Assign Consolidated Logs
- Assign Directories
- Assign Disks
- Assign Event Logs
- Assign Files
- Assign Services
- Assign Shares
- Auto-Config Host Assignment Properties
- Define CSV and W3C Log Entry Columns
- Define Log Entry Columns
- Define Log Entry Columns with Regular Expressions
- Executable Status
- Executable Timeline
- Explicitly Assigned Logs
- File Explorer
- General Executable Properties
- Report Columns
- Report Date/Time Ranges
- Report Security Event Log Filters
- Select Folder or File
- Target Files and Sub-Directories
- Command Line Interface
- Server Configuration
- Agent Configuration
- Troubleshooting
- Best Practices
- Terminology
Corner Bowl Server Manager
SIEM, IPS, Server Monitoring, Uptime Monitoring and Compliance Software
Log Monitor Template
The Log Monitor Template enables you to fire actions when specific entries are detected. Some of the Log Consolidation Templates, such as Event Log Consolidation, Azure AD Audit Log Consolidation and Text Log Consolidation, include post consolidation monitors enabling you to scan consolidated log entries as they are received rather than creating multiple templates, one for consolidation and one for monitoring. Since Syslog monitoring is real-time, Syslogs are the exception to this rule. Log Monitoring is configured via the Monitor Tab found within each supported template's properties view.
To create a new Log Monitor Template
- From the Menu Bar, select File | New. The Create New Object View displays.
- From the Create New Object View, expand Templates | Log Management and finally select Log Monitor. The New Template View displays.
- Use the Sub type drop-down to select the log type.
- Use the Monitor Tab to assign multiple log monitor rules.
Log Monitor Rules
Use the Rules control to manage your log monitor rules.
To add a new log monitor rule
- From the Rules control, click the Add
 button to add a new rule. A new line item is added to the table.
button to add a new rule. A new line item is added to the table. - Use the Name text box to specify a friendly name for the rule.
Note
To include the log monitor rule name in the subject line of an email notification, insert the {MONITOR_RULE_NAME} variable tag in the action's email subject line.
- Use the Rule drop-down to specify the rule type. The following options are available:
| Option | Description |
|---|---|
| Default | Assigned actions are triggered when entries pass the assigned filter. Scheduled monitors, such as Event Log Monitors and Azure AD Audit Log Monitors, group all entries that pass the filter into a table then include the table in assigned action content. Real-Time monitors, such as Syslog Monitors, trigger an action each time an entry passes the filter and include the entry in the assigned action content. |
| Frequency | Assigned actions are fired after the configured threshold has triggered. The less than operand is executed 30 seconds after the top of the minute. |
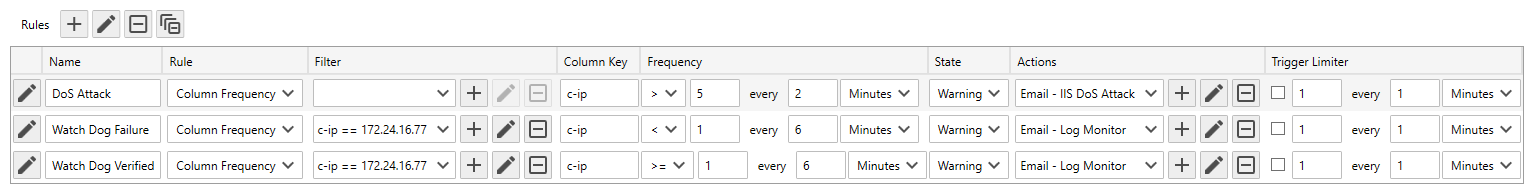
| Column Frequency | When custom columns are defined, for example when monitoring IIS Log Files, unique column values are grouped, then frequency rules applied to each group. This option enables you to, for example, get notified when there is an ongoing DoS attack on your web server. |
| Proximity | Assigned actions are fired after the first filter is triggered then after the second filter is triggered. This option enables you to get notified when the time span between two entries is too great or non-existent. For example, get notified when a text log contains a started message but does not contain a completed message within the configured time span. |
To configure a Default rule type
- Use the Filter drop-down to select the filter to apply.
To configure a Frequency rule type
- Use the Filter drop-down to select the filter to apply.
- Use the Frequency controls to apply the frequency rules (e.g. > 100 times every 5 minutes or < once an hour).
To configure a Column Frequency rule type
- Use the Filter drop-down to select the filter to apply.
- Use the Column Key text box to specify the key of custom column to target.
Note
For Example: When monitoring W3C IIS log files, to get notified when there is an ongoing DoS attack, specify c-ip, the key of the column that contains the client's IP address. In this example, to include the IP address in the subject line of an email notification, insert the {c-ip} variable tag in the action's email subject line.
- Use the Frequency controls to apply the frequency rules. Frequency rules are applied to each unique value found in the column.
To configure a Proximity rule type
- Use the Filter drop-down to select the first filter to apply.
- Use the Proximity Filter drop-down to select the second filter to apply.
- Use the Frequency controls to apply the frequency rules to entries that pass the Proximity Filter.
To configure a actions
- Use the Set monitor state to drop-down to configure the state to set the monitor to once triggered. If you do not want to trigger the state, set the state to OK.
- Use the On Trigger drop-down to assign the actions to fire once the monitor triggers.
- Use the Limit to check box to limit the number of times the actions are fired within the configured time span.