Table of Contents
- Getting Started
- Agent-Based Management
- Common Tasks
- Data Providers
- Directory Services
- Auditing
- Hosts
- Templates
- Template Properties
- Batch Update Templates
- Assign Templates
- Log Management Templates
- SCAP Compliance Monitor
- Active Directory User Monitor Templates
- File and Directory Monitor Templates
- Windows Monitor Templates
- CPU Monitor Template
- Memory Monitor Template
- Disk Space Monitor Template
- Account Lockout Monitor Template
- Audit Policy Monitor Template
- Logon As Monitor Template
- Logon Monitor Template
- Performance Counter Monitor Template
- PowerShell Template
- Process Monitor Template
- RDP Session Monitor Template
- Registry Value Monitor Template
- Service Monitor Template
- SMART Disk Monitor Template
- System Security Monitor Template
- Windows Update Template
- WMI Query Template
- Task Scheduler Template
- Clock Synchronization Template
- Defragment NTFS Disks Template
- Network and Application Monitor Templates
- SSL Certificate Monitor Templates
- Database Templates
- Email Monitor Templates
- SNMP Monitor Templates
- Windows Accounts Templates
- Monitors
- Reports
- Auto-Configurators
- Filters
- Actions
- Schedules
- Environment Variables
- Options
- SNMP
- SSH Shell
- Syslog
- System Reset
- Shared Views
- Active Directory User and Group Filters
- Assign Actions
- Assign Azure Audit Logs
- Assign Consolidated Logs
- Assign Directories
- Assign Disks
- Assign Event Logs
- Assign Files
- Assign Services
- Assign Shares
- Auto-Config Host Assignment Properties
- Define CSV and W3C Log Entry Columns
- Define Log Entry Columns
- Define Log Entry Columns with Regular Expressions
- Executable Status
- Executable Timeline
- Explicitly Assigned Logs
- File Explorer
- General Executable Properties
- Report Columns
- Report Date/Time Ranges
- Report Security Event Log Filters
- Select Folder or File
- Target Files and Sub-Directories
- Command Line Interface
- Server Configuration
- Agent Configuration
- Troubleshooting
- Best Practices
- Terminology
Corner Bowl Server Manager
SIEM, IPS, Server Monitoring, Uptime Monitoring and Compliance Software
SIEM Reports
A SIEM Report queiries the log databases for specific log entries generated from various log types from multiple servers, workstations and network devices, applies log entry filters, applies display options, such as the column order, group by and sort by rules, then lastly, displays, saves or emails the output results.
This report is typically used by SAs and ISSOs that want to analyze and correlate Security Event Logs and data from various sources within their organization's network infrastructure, such as firewalls, intrusion detection systems, and other servers.
In this Topic
Video Tutorial
 How to Generate SIEM Reports for Windows, Ubuntu and Isilon
How to Generate SIEM Reports for Windows, Ubuntu and Isilon
To Create a SIEM Report
- From the Menu Bar select File | New. The Create New Object View displays.
- From the Create New Object View, expand Reports.
- Expand Report | Log Consolidation Reports then select SIEM Report. The Properties View displays.
Report Options
- The Properties View contains 6 configuration tabs.
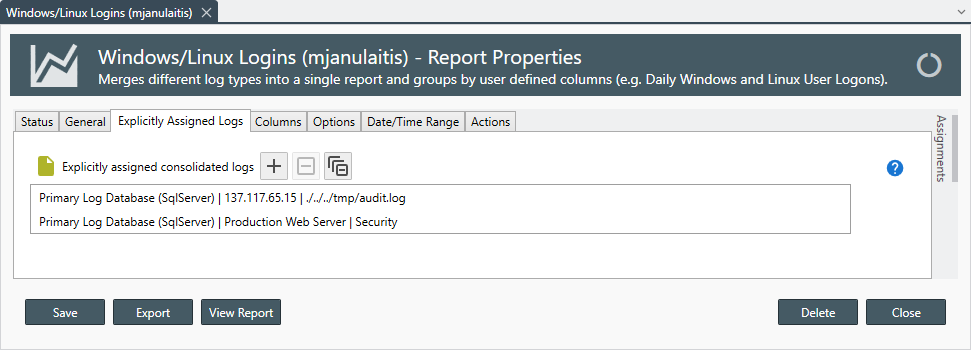
Explicitly Assigned Logs
For more information see: Explicitly Assigned Logs
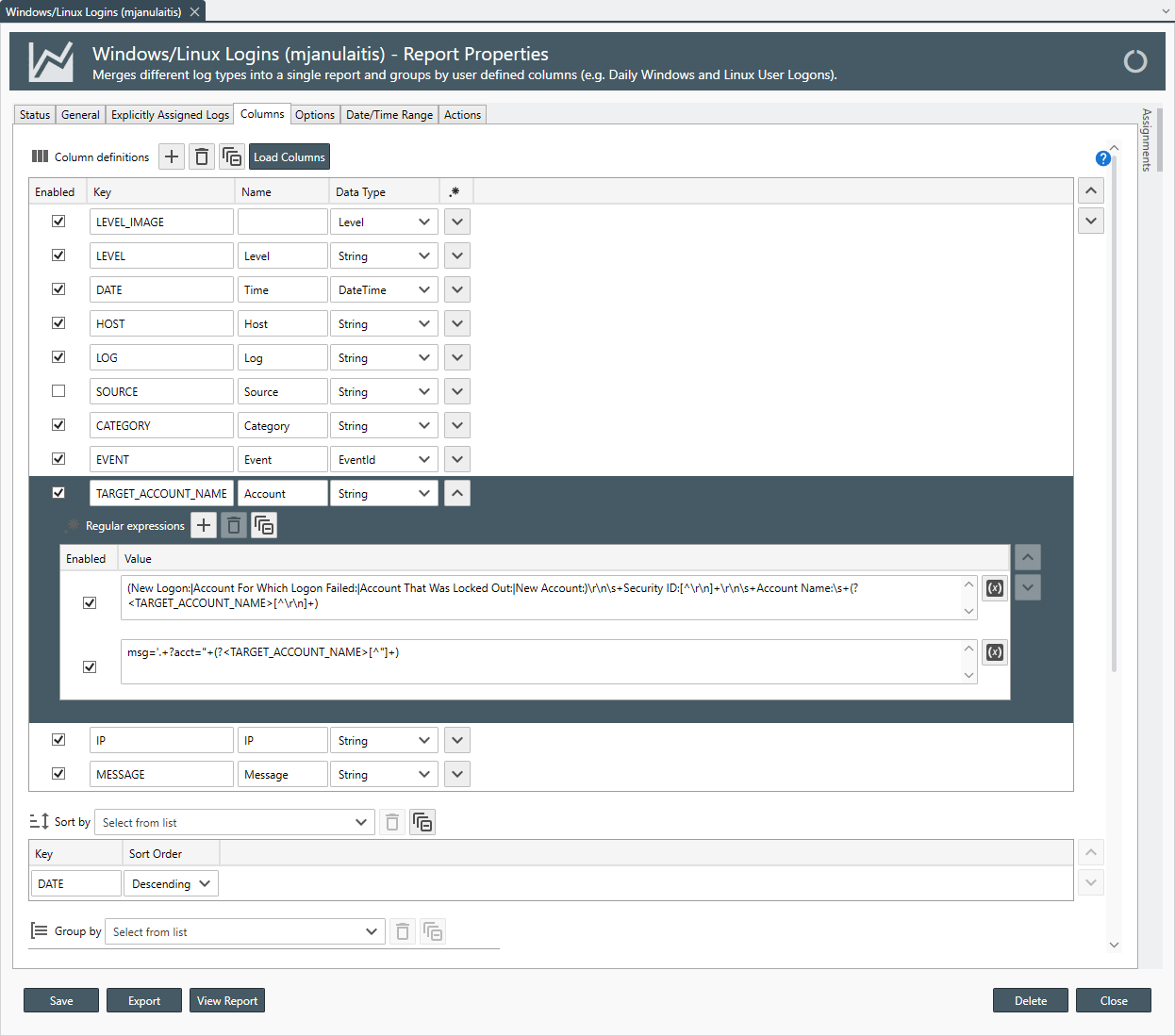
Columns
For more information see: Columns
Note
If you apply regular expressions column definitions in your corresponding log consolidation templates, and the column keys are identical between log types, you do not need to re-apply the regular expressions to the report.
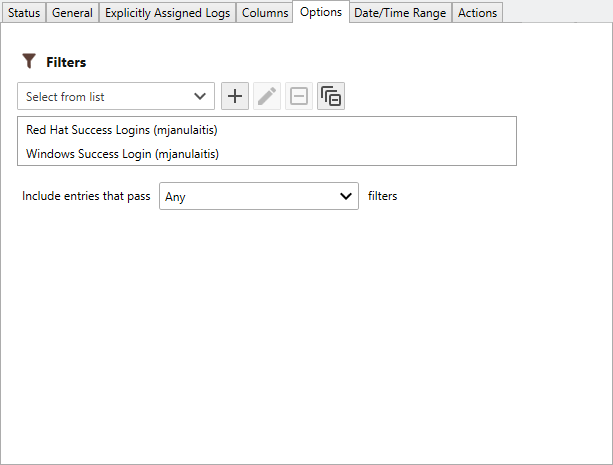
Options
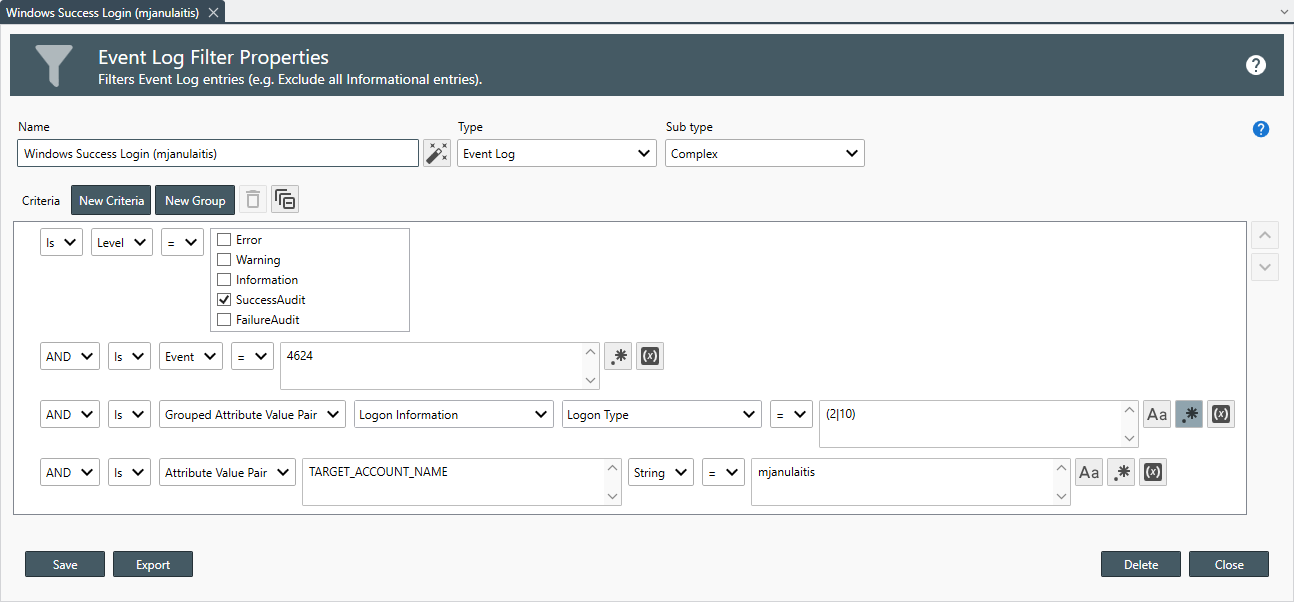
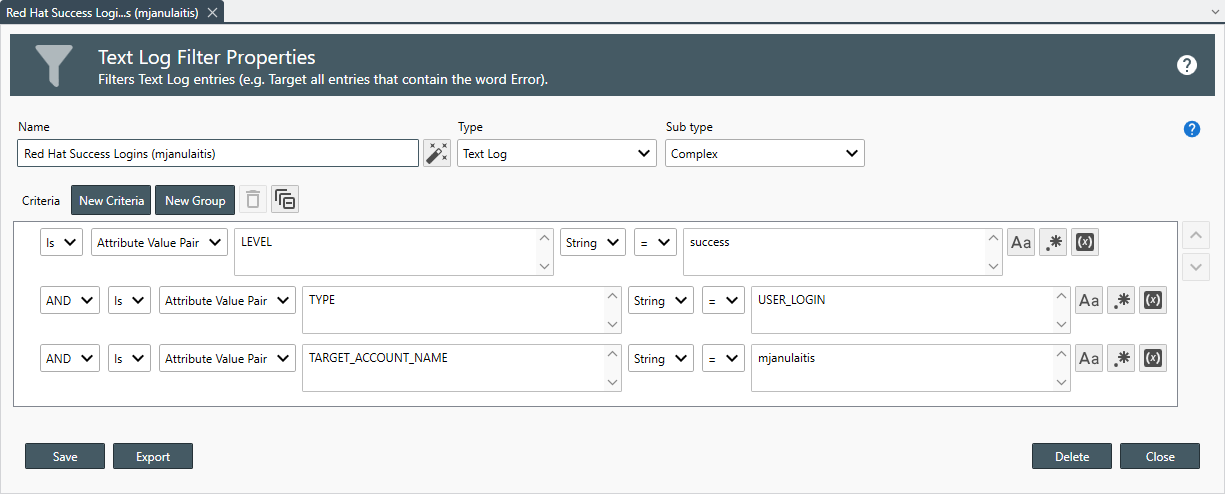
- Use the Filters drop-down to select all of the filters you would like to apply to the report.
Important
Filters are only applied to corresponding log entries types. For example, when you have assigned both an Event Log and a Text Log to the report, Event Log Filters are only applied to Event Log Entries while Text Log Filters are only applied to Text Log Entries.
- Once a filter is assigned, use the Include entries that pass drop-down to select the filter method.The following filter options are available:
| Option | Description |
|---|---|
| All | Include each entry that passes all assigned filters. |
| Any | Include each entry that passes any filter. |
| None | Include each entry that does not pass any of the filters. |
| Ignore | Include all entries. |
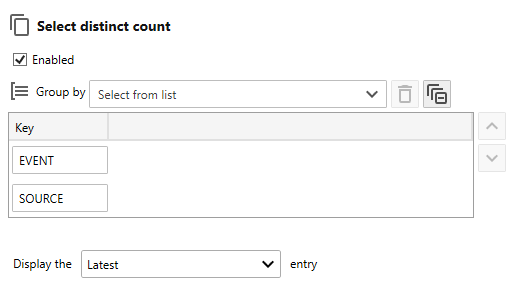
- Use the Select distinct count controls to define a composite key to select a distinct count of entries that match your composite key. For example, generate a report that displays the number of each unique event type, Information, Warning, Critical, Audit Success and Audit Failure or the number of unique entries keyed by Event ID and Source on each assigned host).
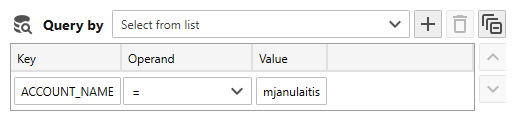
- Use the Query by controls to optimize SQL statements. For example, if the column you want to search for was added using a regular expression column defnition, specify the column key and the value to search for. Once executed, only rows that match your search criteria are returned from the database engine.