Windows Event Log Management Software
Maximize Your Windows Network security
Quickly identify and resolve security issues cost-effectively with Corner Bowl Server Manager, featuring both agent-based and agentless implementation options. Corner Bowl Server Manager is a leading choice for Information Systems Security Managers when managing the extensive security event log data generated by Windows systems that dominate most IT networks. This enterprise solution simplifies Windows event log management, offering capabilities such as event log consolidation, archiving, retention, real-time monitoring, reporting, and the implementation of compliance controls and inline auditing, ensuring a comprehensive and compliant approach to network security.
Event Log Consolidation
- Consolidate Windows Event Logs and Microsoft Application Logs by centrally saving and backing up event log entries to Microsoft SQL Server, MySQL or SQLite.
- Use regular expressions and our security event log parser to parse attribute value pairs to their native data types then save to your RDBMS for internal and external analysis (e.g. integer, decimal and date/time).
- Use our Log Entry Retention Policy Template to automatically delete old event log entries no longer required for compliance and auditing.
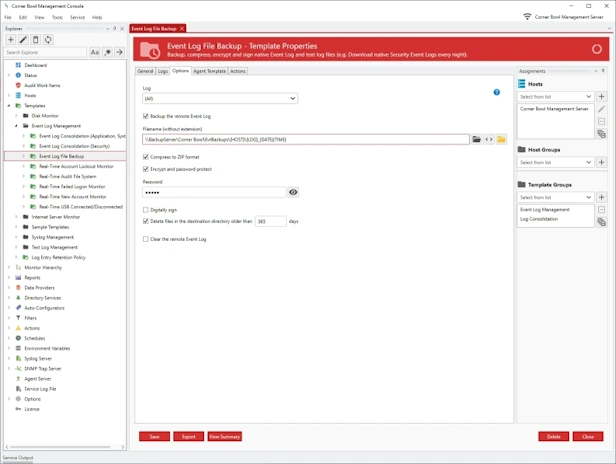
Event Log Archiving
- Centrally archive, zip, password protect, encrypt and digitally sign event log files in their native format.
- Monitor event log file sizes then automatically archive files before Windows archives to backup files to the System32 directory.
- Automatically remove archived event log files once they reach a specific age, such as, 1 year.
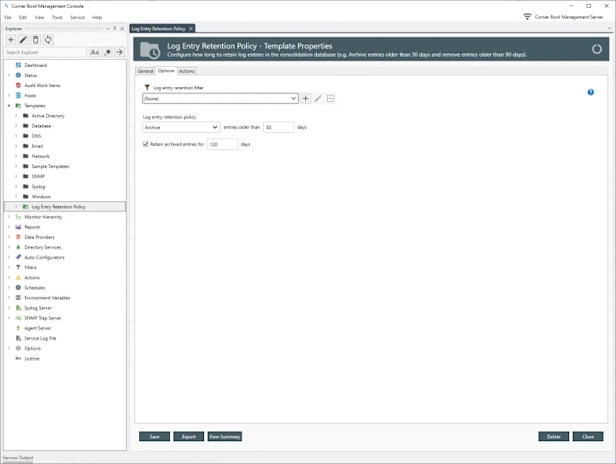
Event Log Entry Retention Policy
- Configure how long to retain event log entries in the log databases, for example, archive entries older than 30 days then remove archived entries older than 1 year.
- Schedule and manually remove event log entries no longer required for analysis or compliance, for example, delete informational event log entries older than 90 days.
- Generate summary reports detailing the log entry retention metadata, for example, the data range and number of entries in each event log database table.
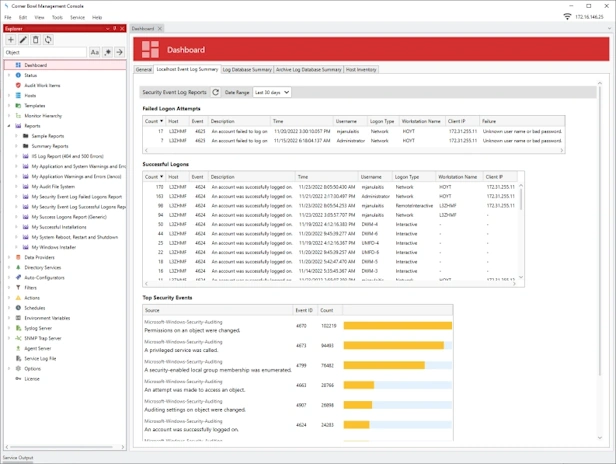
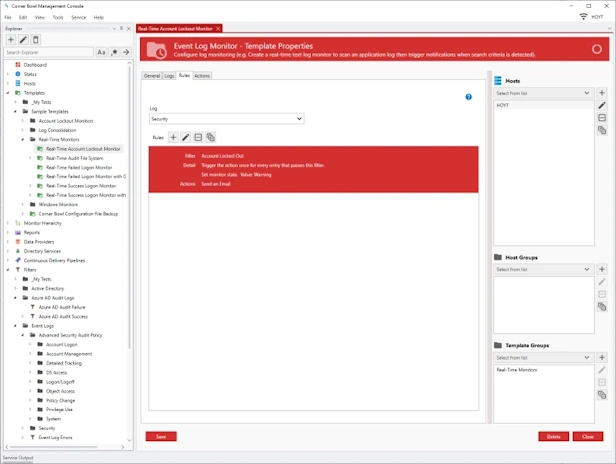
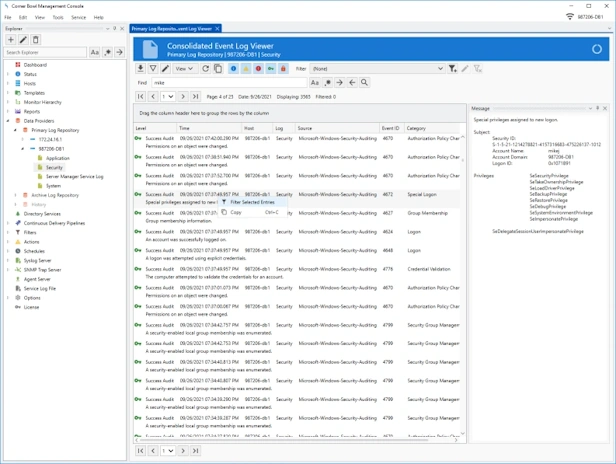
Event Log Monitoring
- Real-time security auditing and monitoring for Windows Event Logs and Microsoft Application Log.
- Automatically detect and apply IPS remediation actions, such as, running a PowerShell Command to block a IP actively involved in a cyber-attack.
- Use regular expressions to parse attribute value pairs to their native data types, for example, integer, decimal and date/time.
- Create Complex Filter Criteria to parse and filter any data typed attribute value pair.
- Apply correlation and frequency rules, for example, get notified when a task starts then completes, or a user fails to login 3 times within 5 minutes.
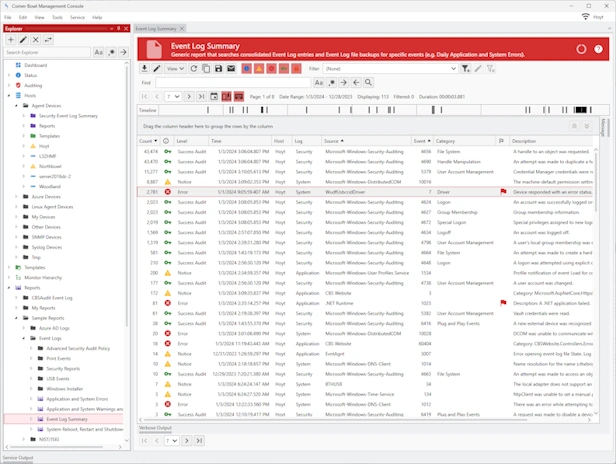
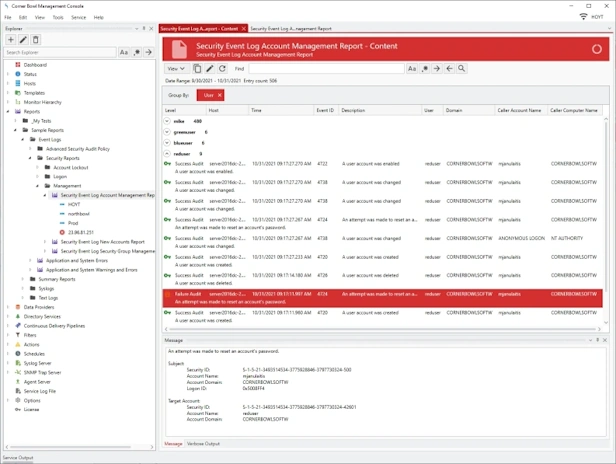
Event Log Reporting
- Choose from 100+ pre-build security event log reports that provide you with the insight and audit controls your need to keep your network secure.
- Customize report layout, event log entry columns, logos, colors, spacing and font sizes.
- Create and customize SIEM Reports that cross multiple log types, such as Windows Event Logs, Azure Entra ID Audit Logs and Red Hat Audit Logs.
Event Log Compliance and Auditing
- Gets you compliant with PCI/DSS, CMMC, NIST, JSIG, CJIS, ISO 27001 and GDPR and more.
- Out-of-the-box pre-build compliance controls and auditing reports for NIST and JSIG.
- Monitor compliance controls and get notified in real-time when any compliance control fails to complete.
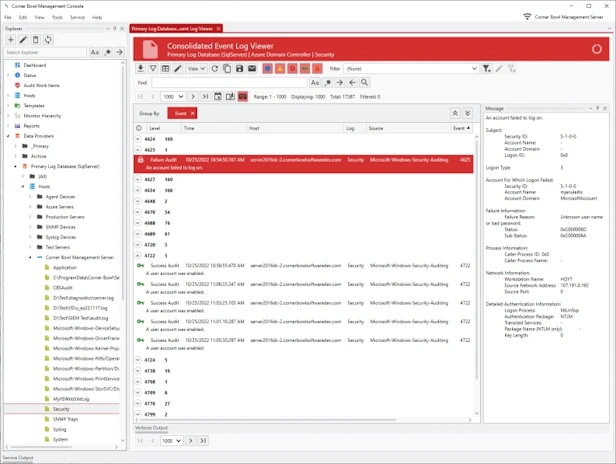
Event Log Analyzer
- Watch Windows Event Logs and Microsoft Application Logs in real-time.
- Page through large log files, search, highlight, view frequencies, mark entries and export result sets.
- Group and sort log entries using complex regular expression driven attribute value search criteria.
Event Log Filters
- Generate filters from real-time and consolidated event log viewers.
- Create simple event log filters with stacked inclusion and exclusion criteria rules.
- Create complex programming style filters from event log entries that include recursive groups, logical operands, categories, and regular expression driven values.
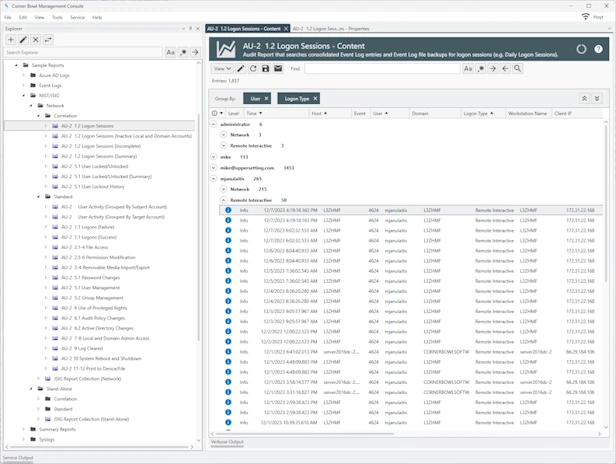
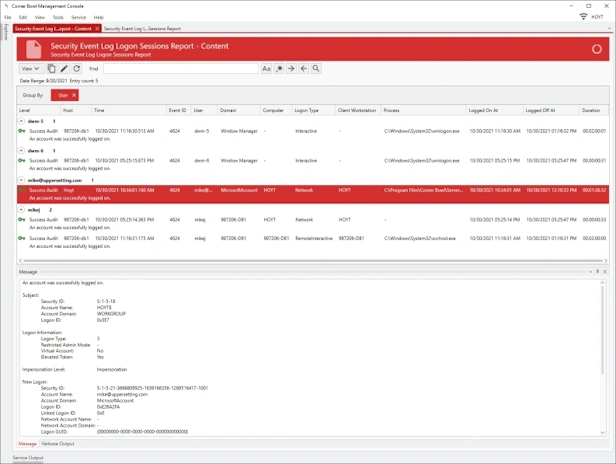
Event Log Entry Correlation, IDS and IPS
- Includes pre-built event log entry correlation reports such as Logon Sessions and Account Lockout/Unlock.
- Group event log entries by column values then trigger alerts based on number of event log entries in each group.
- Implement IDS and IPS remediation responses to active cyber-attacks.
Why do you need an Event Log Management Software Tool?
As an Information Systems Security Manager (ISSM), using an Event Log Management tool on your network offers several key benefits:
- Security Monitoring and Incident Response: Security event logs provide critical information about network activity. By archiving these security event logs, you can monitor for potential security threats, anomalies, and unauthorized access attempts. In the event of a security incident, these event security logs are invaluable for understanding what happened and how to respond effectively.
- Compliance and Audit Trails: Many industries are subject to regulatory compliance standards such as, PCI/DSS, CMMC, NIST, JSIG, CJIS, ISO 27001 and GDPR, that require the retention and protection of security event log data. An Event Log Management tool helps in maintaining comprehensive records, ensuring that your organization meets these regulatory requirements.
- Performance and System Health Monitoring: Event logs can reveal issues related to system performance and health. By analyzing these event logs, you can proactively address potential problems before they escalate, ensuring the smooth operation of your IT infrastructure.
- Forensic Analysis and Historical Data: In the case of a breach or system failure, having historical event log data is crucial for forensic analysis. It allows you to trace back the sequence of events, identify the root cause, and implement measures to prevent future occurrences.
- Efficient Data Management: Such tools usually offer features like automated event log consolidation, parsing, and archiving. This automation saves time and resources, allowing you and your team to focus on more critical tasks.
- Customizable Alerts and Reports: Many Event Log Management tools offer customizable alerts and reporting features. This means you can set up notifications for specific events or patterns, enabling a quicker response to potential issues.
- Centralized Event Log Management: These tools typically allow for centralized management of event logs from various sources across your network. This centralization makes it easier to manage and analyze data from a single, unified platform.
Other Software Components
Related Links
Video Tutorials
Testimonials
Last Updated: August 25th, 2024