Security Information and Event Management (SIEM)
Maximize your network security, implement compliance controls and prove compliance to auditors
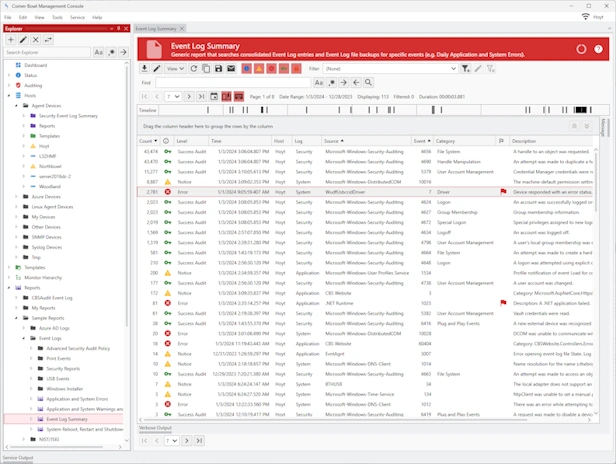
Event Log Management
Event Log Consolidation | Event Log Monitoring | Event Log Analyzer
Agent-based and agentless event log consolidation, backups, archiving, retention, parsing, real-time monitoring and security audit reporting.
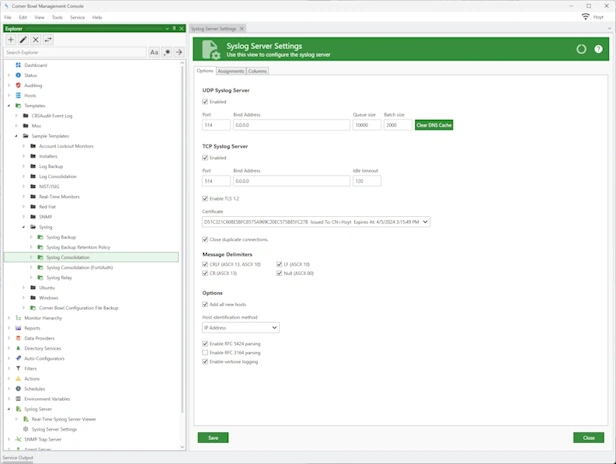
Syslog Server
Syslog Consolidation | Syslog Monitoring | Syslog Analyzer
Centrally manage all of your hardware devices with our high throughput UDP and TCP Red Hat, Ubuntu and Windows Syslog servers.
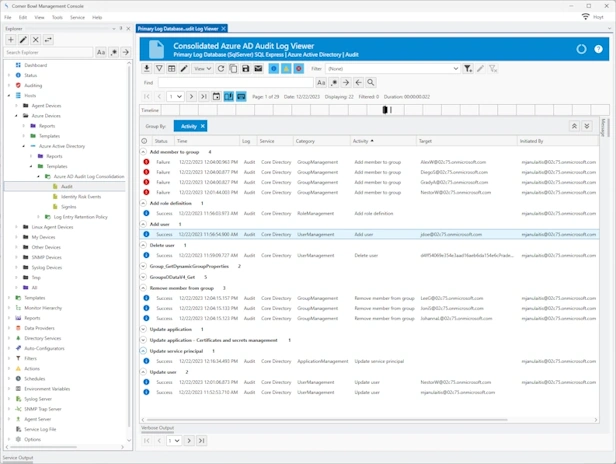
Azure Microsoft Entra ID Audit Log Management
Audit Log Management | Audit Log Monitoring | Audit Log Analyzer
Cloud-based and on-premises Azure Microsoft Entra ID and Office 365 audit log, sign-in log and identity risk events log management.
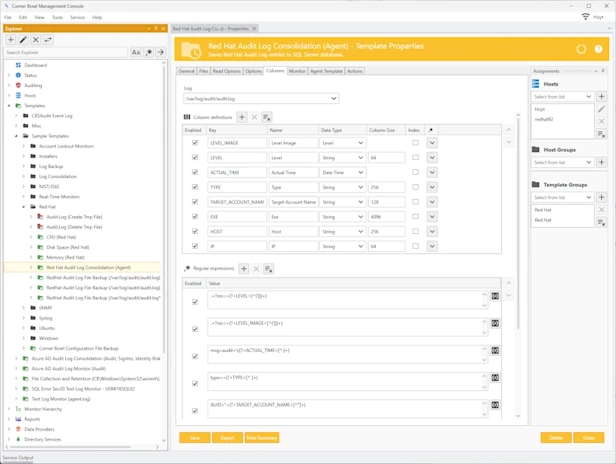
Linux, Red Hat and Ubuntu Audit Log Management
Linux Log Consolidation | Linux Log Monitoring | Linux Log Analyzer
Agent-based Linux, Red Hat Enterprise Linux, CentOS and Ubuntu log management to meet all of your compliance and auditing requirements.
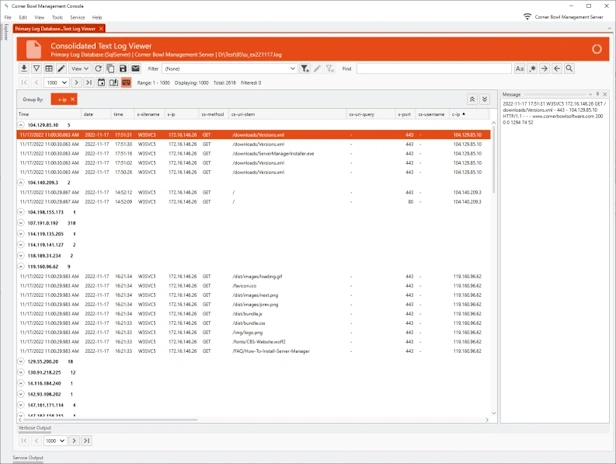
Text Log Management
Text Log Management | Text Log Monitoring | Text Log Analyzer
Centrally consolidate, backup, archive, retain, parse, monitor and analyze W3C, CSV, IIS Logs, Windows firewall logs and any other text-base log file on both Windows and Linux.
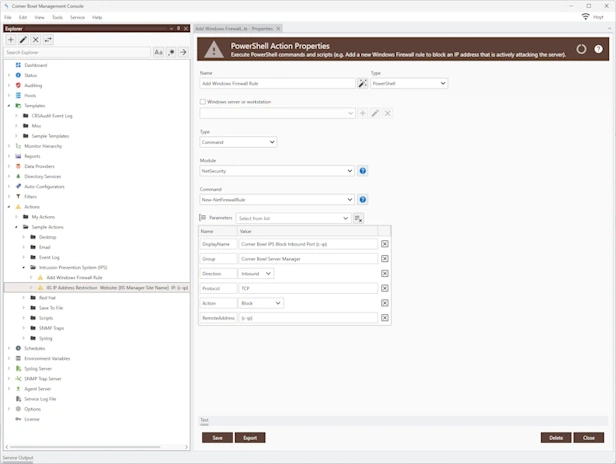
Threat Detection, Notification and Remediation
Intrusion Detection System (IDS) | Intrusion Prevention System (IPS)
Detect intrusions in real-time, notify and take meaningful action to automatically block active cyber-attacks and prevent new cyber-attacks.
Why do you need a SIEM Software Tool?
SIEM (Security Information and Event Management) software is an essential tool for modern businesses, offering comprehensive security management solutions. It combines several security practices, such as the collection, analysis, and presentation of security data, into one platform. Here are the key reasons why a SIEM tool is necessary:
- Centralized Security Data Analysis: SIEM software gathers and analyzes data from various sources within an organization, including network devices, servers, and endpoints. This centralized approach helps in detecting unusual behavior or anomalies that could indicate a security threat.
- Real-time Monitoring and Alerting: SIEM tools provide real-time monitoring of an organization's IT environment, enabling immediate detection of potential security incidents. This prompt detection is crucial for minimizing the impact of security breaches.
- Compliance Management: Many industries have regulatory requirements regarding data security and privacy. SIEM helps organizations comply with these regulations, such as CMMC, NIST, JSIG, CJIS, PCI/DSS, GDPR and ISO 27001, by providing tools for logging, data protection, and report generation.
- Advanced Threat Detection: Utilizing advanced analytics, SIEM software can identify sophisticated cyber threats. This includes the detection of malware, insider threats, and advanced persistent threats (APTs), which might otherwise go unnoticed.
- Incident Response and Forensics: In the event of a security incident, SIEM tools assist in understanding the scope and impact of the breach. They provide detailed information that is vital for effective incident response and forensic analysis.
- Automated Security Management: SIEM software often includes automation capabilities, reducing the workload on security teams. This automation can include the correlation of security alerts, threat prioritization, and even initiating defensive actions.
- Enhanced Visibility into Network Activities: SIEM gives a comprehensive view of an organization's network activities. This visibility is key for identifying unauthorized access, data exfiltration, and other security risks.
- Cost-Effectiveness: Although implementing a SIEM solution involves initial costs, it can be cost-effective in the long run. By preventing significant security breaches, it saves the organization from potential losses due to data breaches, system downtimes, and reputational damage.
Other Software Components
Related Links
Video Tutorials
Testimonials
Last Updated: March 21st, 2024