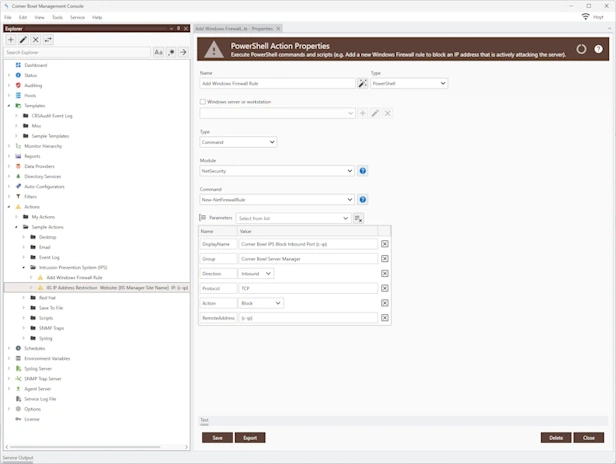
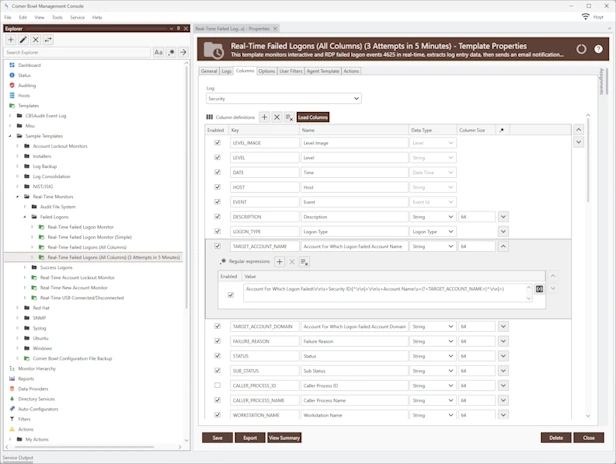
Protect your network with our Intrusion Prevention System (IPS) software, a vital component against cyber-attacks. Our IPS offers real-time defense, proactively identifying and neutralizing risks before they harm your production environments. It's designed to detect and block active cyber-attacks and minimize downtime, making it an essential component of your cybersecurity strategy. With advanced threat detection, customizable intrusion detection policies, and comprehensive reporting, our IPS not only secures your network but also enhances its performance, offering peace of mind and cost-effective protection.