File Integrity Monitoring Software
Monitor and detect virus and ransomware attacks
What is Corner Bowl File Integrity Monitor?
Corner Bowl File Integrity Monitor is an extensive enterprise-class software monitoring and management tool for IT professionals that enables your organization to continuously monitor operating system executables and dlls, application and mission critical data files, changes made to any file's content, attributes, access permissions, and file access on both Windows and Linux servers and workstations. Corner Bowl File Integrity Monitor will help you fulfill compliance requirements for CJIS, CMMC, JSIG, NIST, GDPR, HIPAA, PCI/DSS and SOX.
How does Corner Bowl do it?
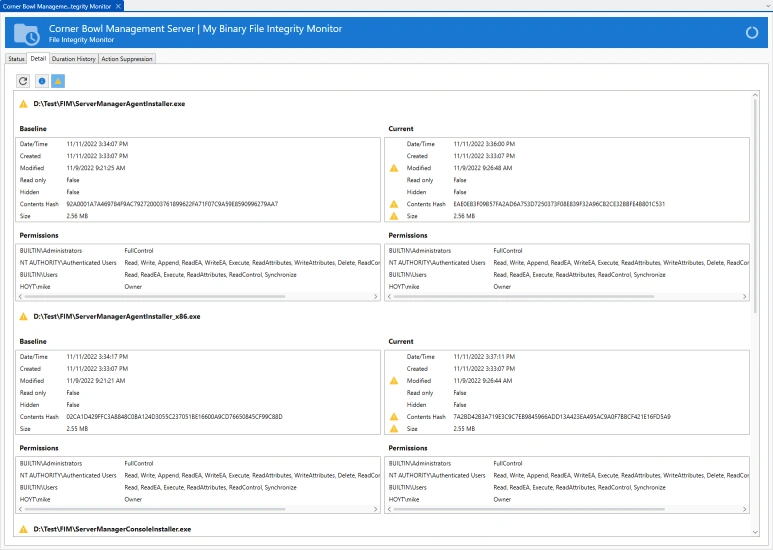
Baseline Scanning
Corner Bowl Software's File Integrity Monitor scans directories using Windows Shares and SSH/SFTP to create file access, file attribute and file content baselines then continually re-scans to let you know when a file is accessed, modified or deleted. Access Permissions are scanned on Windows Servers using WMI.
Real-Time Object Access Auditing
If you want to know the user that modified a file on a Windows Server, enable Object Access Auditing on your Windows Server and you will get notified in real-time the instant a user accesses a file along with the IP address the access was made from. Please note, Object Access Auditing monitoring requires either a Server Manager or an Event Log Manager license.
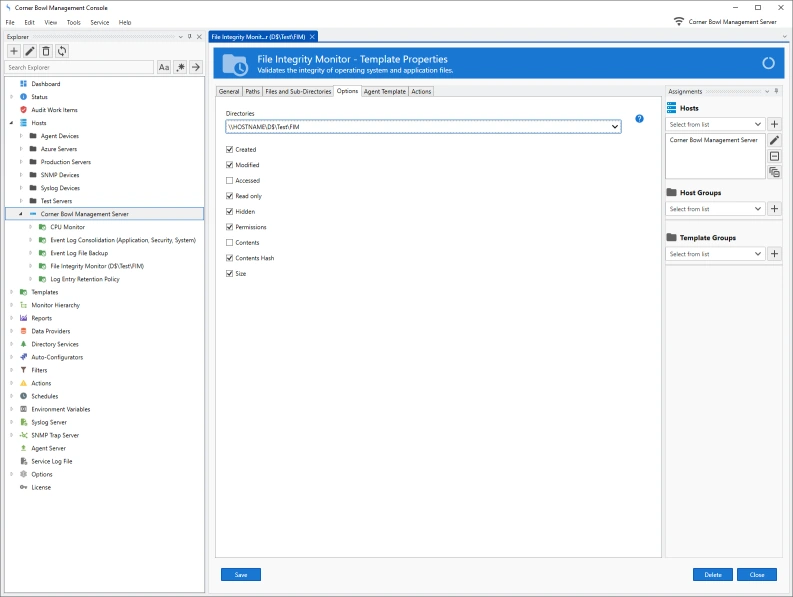
File Integrity Monitoring Options
| Accessed | Notifies you when a file is accessed. |
| Modified | Notifies you when a file is modified. |
| Created | Validates the file was not replaced with another file that contains a different creation time. |
| Attributes | Validates file attributes such as Hidden and Read-Only have not changed. |
| Access Permissions | Performs and exhaustive scan of file permissions then notifies you when any permissions have been added, modified or removed. |
| File Contents Hash | Performs a hash using the file contents then notifies you when any bits have changed. |
| File Contents | Baselines the entire file contents then validates no bits have changed. |
| File Size | Notifies you when the file size changes. |
Who Requires File Integrity Monitoring?
| PCI DSS | Payment Card Industry Data Security Standard (Requirement 11.5)[3] |
| SOX | Sarbanes-Oxley Act (Section 404)[4] |
| NERC CIP | NERC CIP Standard (CIP-010-2)[5] |
| FISMA | Federal Information Security Management Act (NIST SP800-53 Rev3)[6] |
| HIPAA | Health Insurance Portability and Accountability Act of 1996 (NIST Publication 800-66)[7] |
| SANS | Critical Security Controls (Control 3)[8] |
Source: Wikipedia
Other Software Components
Related Links
Video Tutorials
Testimonials
Last Updated: August 25th, 2024