How to Configure Microsoft SQL Server
The software includes an onboarding wizard which is what I am going to use to configure Microsoft SQL Server.
- To open the wizard select Tools -> Onboarding Wizard.
- Once you skip past the introduction page you are prompted to assign Logon as Credentials. In order to pull Security Event Log Entries from remote sources we need to assign the service with Domain Administrator credentials. If the server the service is running is not on a domain then local admin credentials will suffice. In the later case, you will need to configure impersonation for each remote host you want to download Event Logs from. I am not on a domain so I'm going to setup local administrator credentials.
- Once entered, click Update and Restart.
- If you look in the upper right corner you will notice the connection icon briefly displays the disconnect icon while the service restarts and the console re-connects.
- Now that the service credentials are set we can continue.
- The next tab is the Email Settings tab which for this video is out of scope so let's just skip past this step.
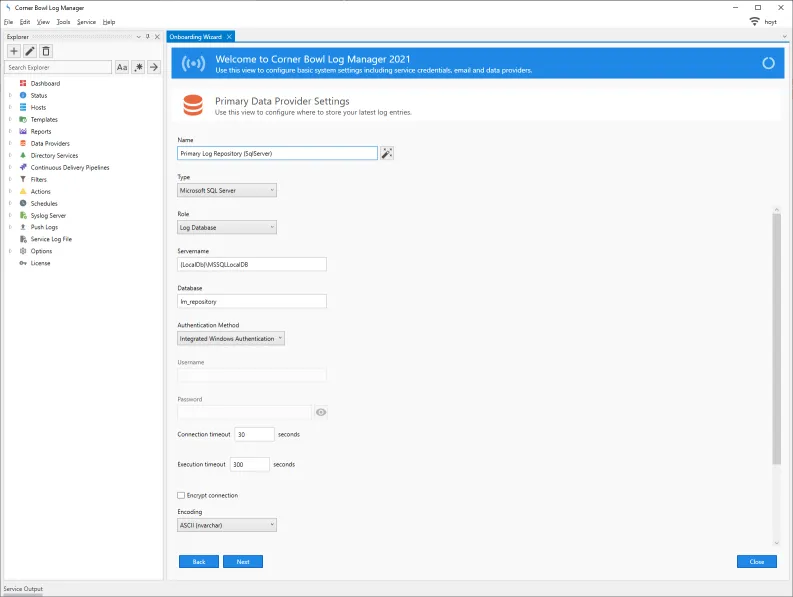
- The next tab is the Primary Data Provider Settings tab which is where we need to change the default File System configuration to Microsoft SQL Server.
- Under the Type drop-down select Microsoft SQL Server.
- Notice the name references the file system. If we click on the Generate Name button the name is updated and now references SQL Server.
- Notice the role is set to Log Database. There are three roles. Log Database, Archive Log Database and Auxiliary Log Database. The Log Database contains all of the latest consolidated log entries. The Archive Log Database contains older entries, for example entries older than 14 days. Finally, Auxiliary Log Databases can be used to load older database backups for auditing and analysis purposes.
- Specify the hostname your SQL Server is installed.
- The database name, lm_repository, listed will be automatically created in a moment.
- Specify the authentication method to use, either Integrated Windows Authentication or SQL Server.
- I am going to use Integrated Windows Authentication which means the account the service is running under is used.
- If at a later time you find queries are timing out you can increase the execution timeout here.
- Finally, click the Next button.
- Once the database and control tables are created the wizard will advance to the Archive Data Provider Settings tab.
- Notice now the Role is set to Archive Log Database.
- Under the Type drop-down select Microsoft SQL Server.
- Update the name.
- Notice the database name is now set to lm_archive.
- Specify the authentication method.
- Finally, click the Next button.
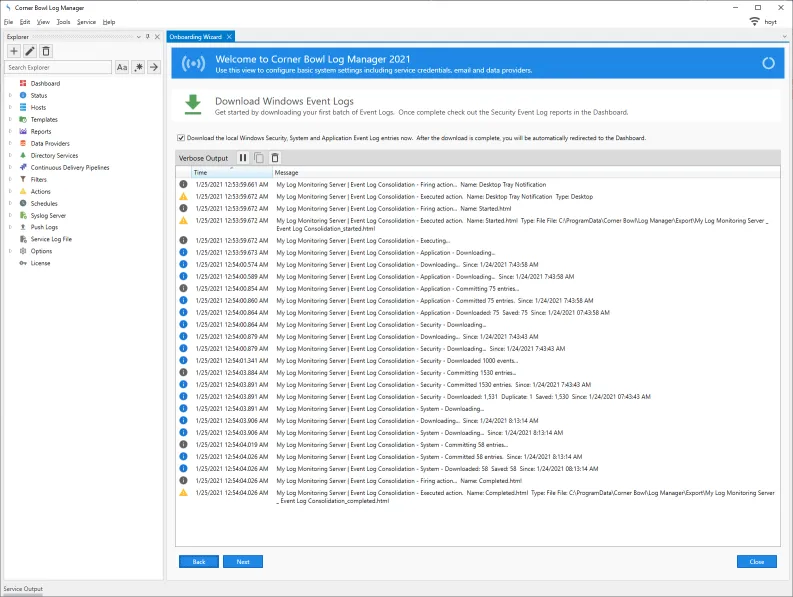
- The last step consolidates the Application, System and Security logs from system the service is installed to the log repository database we just configured.
- Click Next and you can verify the software is able to populate the database we just configured.
- We have now configured the databases.