Object Access Auditing
Object Access Auditing enables you to know in real-time the instant a user accesses, modifies or deletes a file. First, we need to configure Object Access Auditing on the target server.
Configuring Object Access Auditing
- If monitoring a non-domain computer, from Administrative Tools select Local Security Policy.
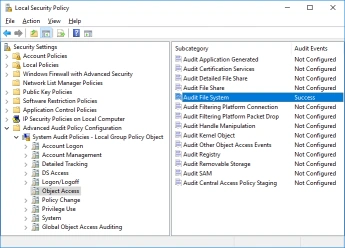
- Expand Advanced Audit Policy Configuration then expand Object Access.
- From the detail view double-click Audit File System.
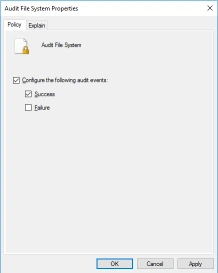
- From the Audit File System Properties dialog check Success then OK.
- For more information see Microsoft's documentation.
Next, we need to configure the target folder.
- Open Explorer then navigate to the target folder, right click and select Properties.
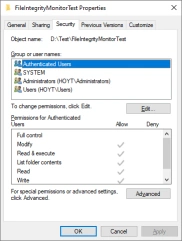
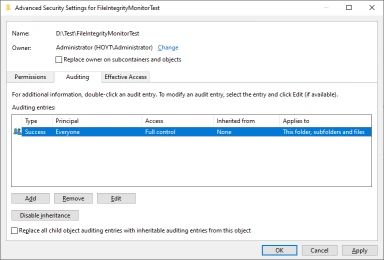
- From the File Properties dialog select the Security tab then click the Advanced button.
- From the Advanced Security Settings dialog select the Auditing tab. If you are prompted to continue, click the Continue button. Next click the Add button.
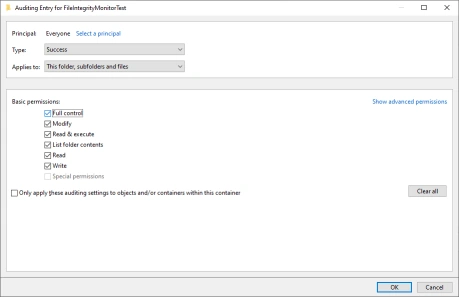
- From the Auditing Entry dialog click the Select a principal link.
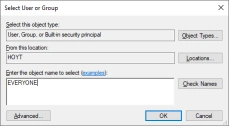
- From the Select User or Group dialog type EVERYONE then click OK.
- Back in the Auding Entry dialog check all of the options then click OK.
- Back in the Advanced Security Settings dialog verify the new entry was added then click OK.
- Finally, back in the File Properties dialog click OK.
- For more information see Microsoft's documentation.
Configuring Real-Time File System Auditing
By default, a Real-Time Audit File System template is pre-installed in the following location:
Templates/Sample Templates/Real-Time Monitors/Real-Time Audit File System
If the template cannot be found it is most likely because you already installed the software prior to the release of this template.
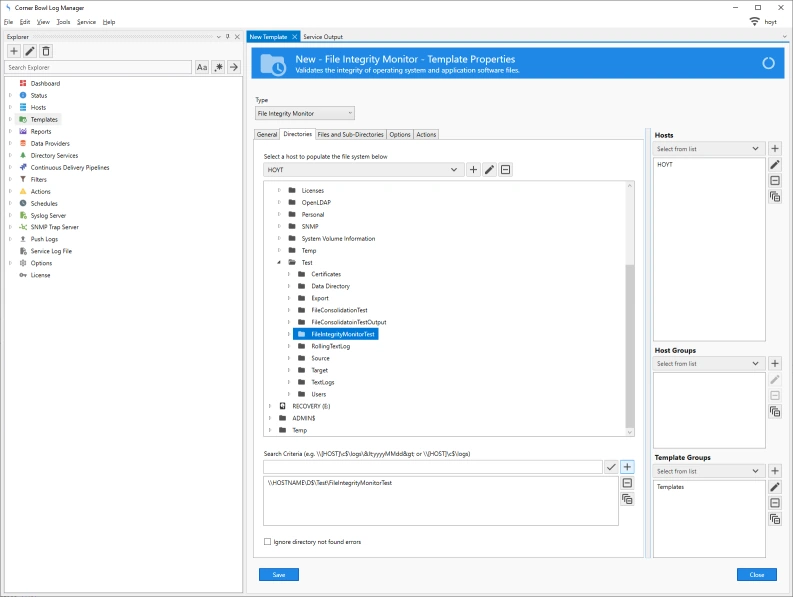
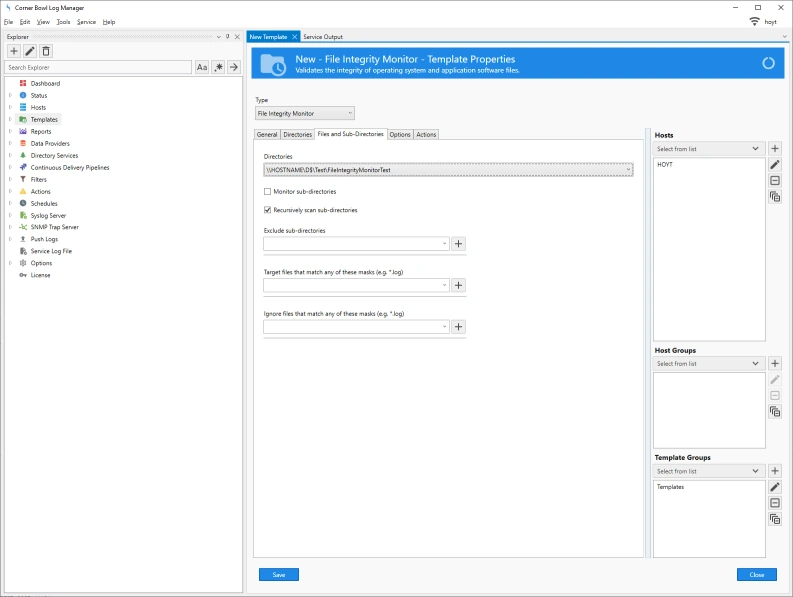
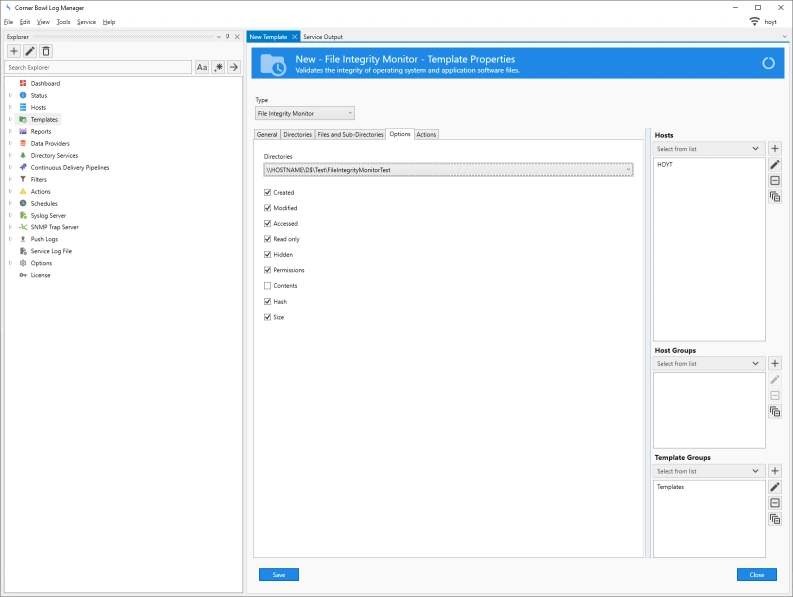
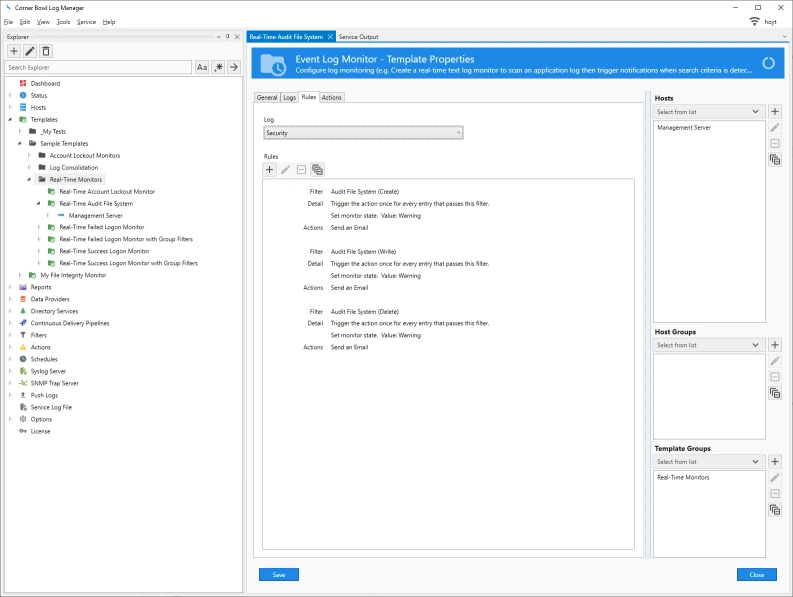
- Right click on the Real-Time Audit File System template then select Template Properties. The Template Properties view displays.
-
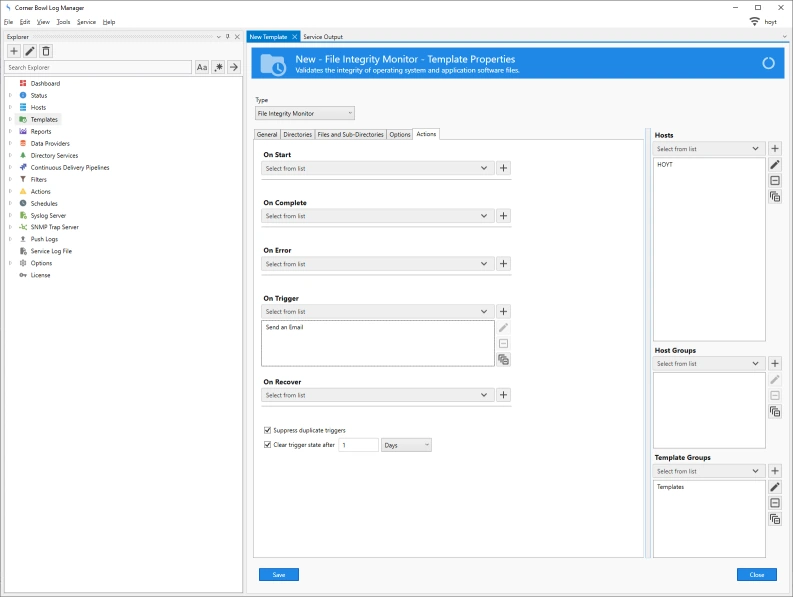
If you select the Rules tab you can see three filters and actions pre-assigned. These filters are assigned to track Create, Write and Delete Audit File System events.
Make sure to assign an email address to the pre-installed Send an Email action otherwise you won't receive notifications.
- Finally, from the Hosts drop-down select the target host to monitor then click Save.
Testing Real-Time File System Auditing
To test we can simply create a new text file in the target directory, open the file in a text editor, modify and save it, then finally delete the file. Once complete, you will see 4 messages in your email. One for the creation of the file, one for the update of the file contents and then Microsoft fires two absolutely identical Events for the delete operation which is unfortunate however the end result is the same, a notification is received.
 button.
button.