File System Auditing with Server Manager
October 21st, 2021
In this article I am going to:
- Show you how to get notified in real-time in when a user creates, modifies or deletes a file.
- Show you the built-in Real-Time Audit File System Template and the associated filters that trigger when files are created, modified and deleted.
- Show you how to enable Object Access Auditing on a non-domain server then apply auditing to a directory.
- Finally I'll put it all together and show you various alerts.
Getting Started
- First login with your Windows administrator credentials.
- Server Manager includes some pre-built Templates which you can use as a starting point.
- If you are not familiar with Corner Bowl, templates contain information such as the log files to monitor, the filters to apply and the actions to execute.
- Templates are then assigned to one or many hosts to create monitors.
OK let's look at the Real-Time Audit File System Template.
The Real-Time Audit File System Template
- From the Explorer View expand Templates / Sample Templates / Real-Time Monitors / Real-Time Audit File System.
- To open the properties view, right click and select Template Properties.
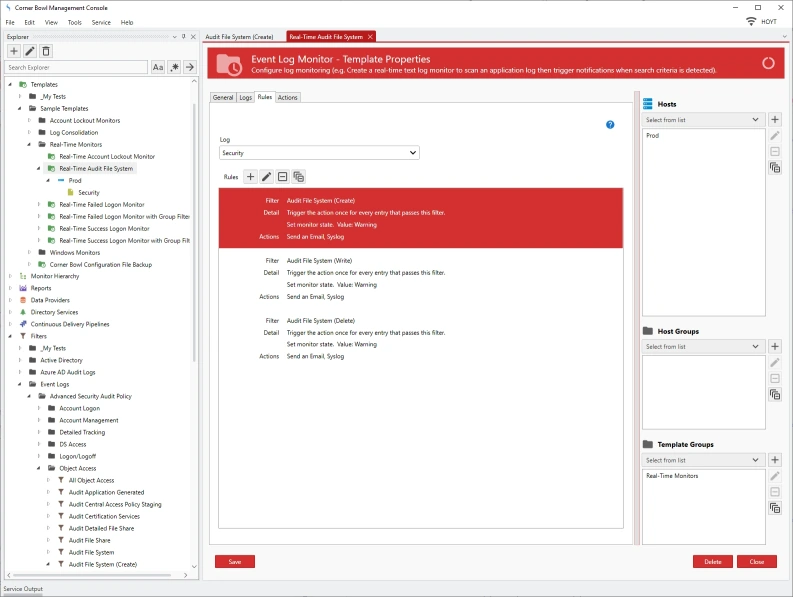
- The Template Properties View displays with 4 tabs.
- The General Tab let's you assign the schedule to run. This is a real-time monitor so we can just leave the schedule as it is set to Real-Time.
- The Logs Tab let's you assign the logs to monitor. Here we can see the Security Log is selected.
- The Rules Tab let's you assign filters and actions.
- Lastly, the Actions Tab enables you to assign error actions, for example when access to the server is blocked or the server is offline.
The Rules Tab
- Back in the Rules tab, we can see there are three filters applied. One to trigger when a file is created, another for when a file is modified, and lastly when a file is deleted.
- You can find these filters in the Explorer View under Filters / Event Logs / Advanced Security Audit Policy / Object Access.
- You will find a general Audit File System Filter which contains the Event IDs as defined by Microsoft.
- Then just below we can see the Create, Delete, Read and Write filters.
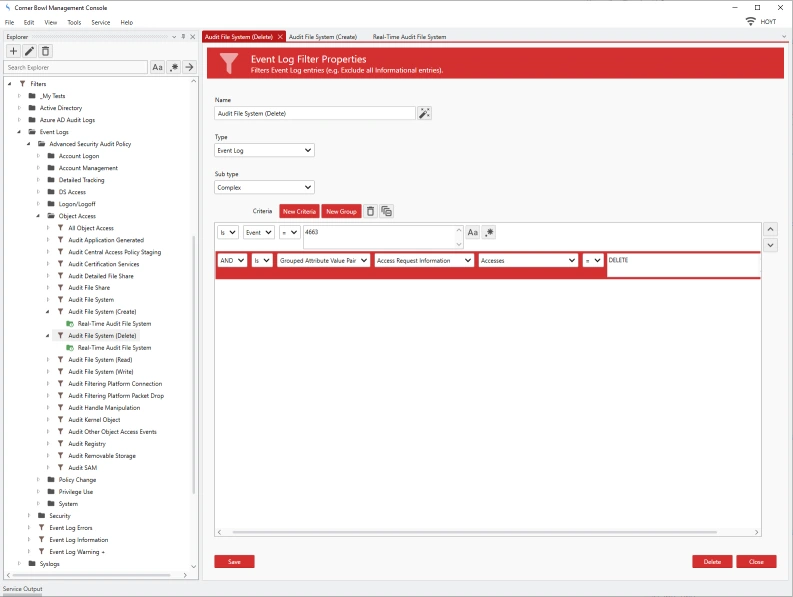
- To view the Filter Properties, right click on the filter and select Properties. The Filter Properties View displays.
- We can see the filter is looking for Event ID 4663 and is looking for a the Group Attribute Value Pair where the Group is 'Access Request Information' the Attribute is 'Accesses' and the Value is 'WriteData (or AddFile)'
- If I look at the other filters we can see the same ID is used but the criteria has different values, in this case DELETE.
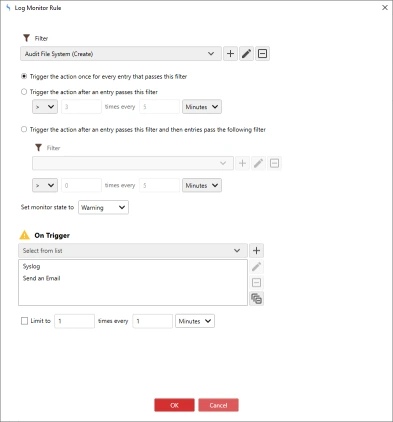
- Back in the Template Properties view, double-click the first item in the Rules list. The Log Monitor Rule dialog displays.
- Here we can see the filter that is applied, in this case Audit File System (Create) and the actions to execute when an Event Log Entry passes the filter.
- For demonstration purposes, I am going to also assign a syslog action to each log monitor rule.
- Next, I Assign the host I want to monitor.
- Ok so that's the Template. Finally, click Save.
- Back in the Explorer View we now see the host listed under the Real-Time Audit File System template.
How To Configure Object Access Auditing
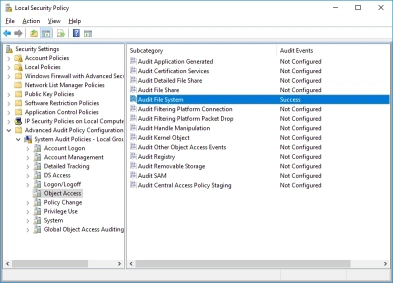
- From the server you want to monitor, open the Control Panel then select Administrative Tools then Local Security Policy.
- Expand Advanced Audit Policy Configuration / System Audit Policies \ Object Access
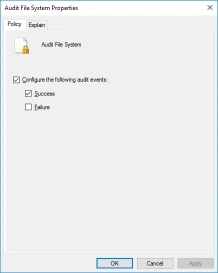
- Then in the right pane double-click Audit File System. The Audit File System Properties view displays.
- Check Configure the following audit events then Success.
- Finally click OK to save your changes.
How To Configure Directory Auditing
- Next, we need to configure the directory to audit. Instructions from Microsoft.
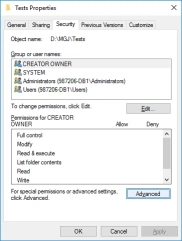
- Open Windows Explorer, locate the directory to audit, right click and select Properties.
- From the Directory Properties view, select the Security tab then click Advanced.
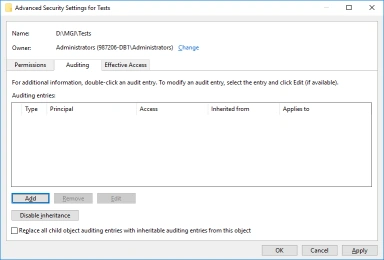
- From the Advanced Security Settings view, select the Auditing tab then click Add.
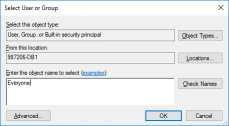
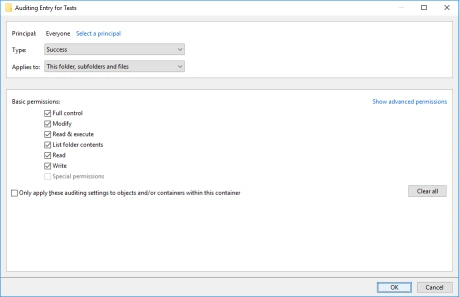
- From the Auditing Entry Properties view, click on Select a principal.
- From the Select User or Group dialog select the account you would like to audit, for example Everyone, then click OK.
- From the Audit Entry Properties view, check Full Control then click OK.
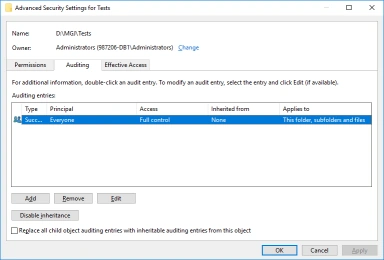
- The Advanced Security Settings view now lists the new audit policy.
- Click OK to save your changes.
Testing the File System Auditing
- Back in the Corner Bowl Management Console, from the Explorer View, right click on the Security node under the host, then select Watch.
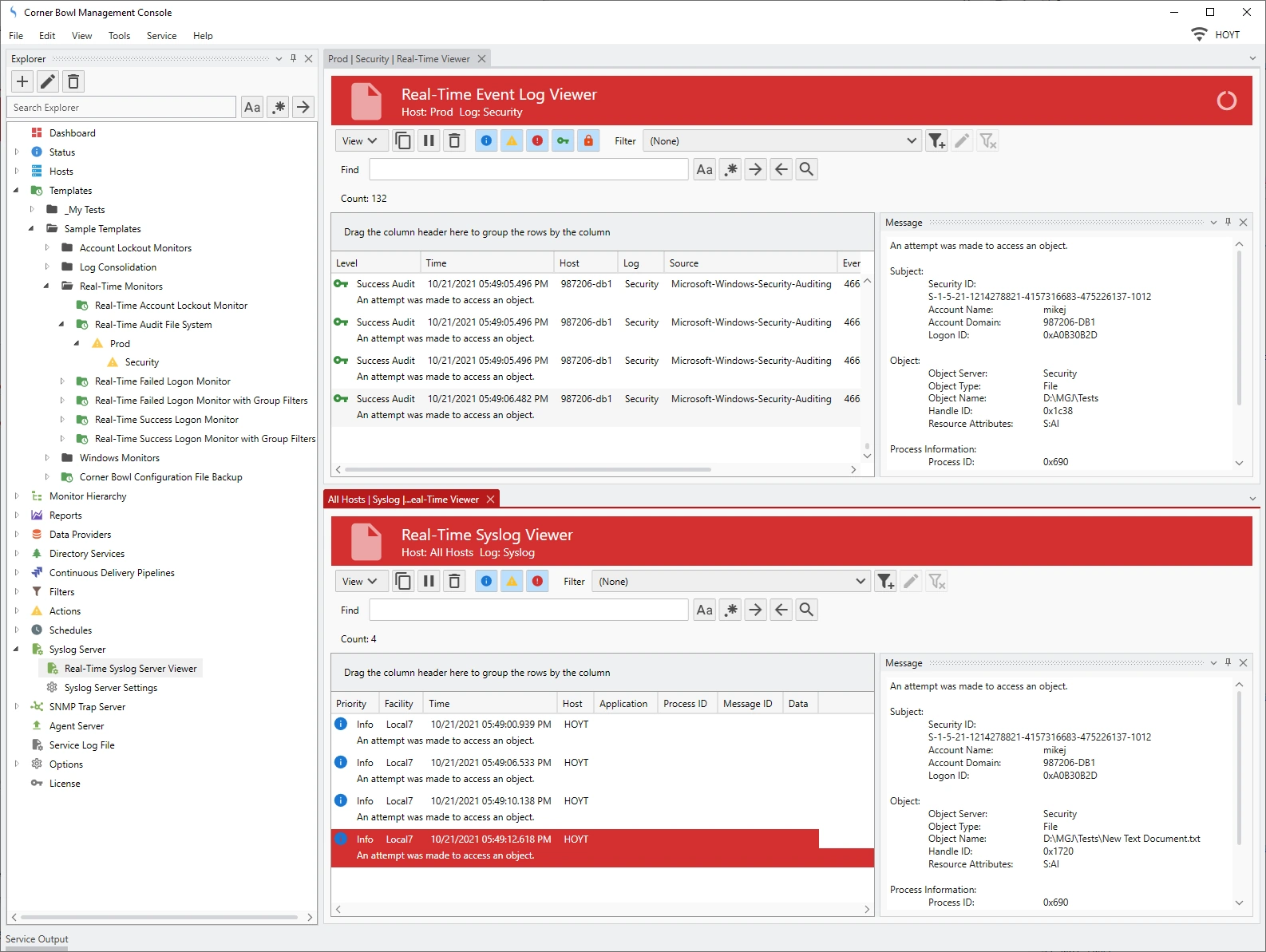
- The Real-Time Event Log Viewer displays.
- Remember earlier I added the Syslog action to the monitor rule. To view the syslog messages I need to open the Real-Time Syslog Viewer.
- To open the Real-Time Syslog Viewer, from the Explorer View, expand Syslog Server then select Real-Time Syslog Server Viewer.
- The Real-Time Syslog Viewer displays.
- Next, I am going to split the screen so I can see both real-time viewers at the same time.
- On the server you are monitoring, create a file, open the file, write to the file, then delete the file.
- Back in the Corner Bowl Management Console we see the results.
- Notice the Syslog entries. Selecting each entry reveals the Event Log Entry that was triggered. Notice also the account name of the user that made the changes is listed in the Security Event Log message.
- Also notice, Microsoft fires 2 identical entries for the delete.
Ok that's File System Auditing with Corner Bowl Server Manager.
October 21st, 2021