What is Event Log Manager?
Corner Bowl Event Log Manager is an extensive enterprise-class SIEM software monitoring, event log management, security and compliance tool for IT professionals that includes centralized log consolidation to native format, SQL Server, MySQL and SQLite, 100+ pre-built Security Event Log Auditing and Compliance Reports, real-time and scheduled event log monitoring, a powerful event log analyzer with paging support for large files, Azure Active Directory Audit Log support, regular expression support, and more. Event Log Manager will help you fulfill compliance requirements for CJIS, CMMC, JSIG, NIST, GDPR, HIPAA, PCI/DSS and SOX.
Event Log Consolidation
- Consolidate Windows Event Logs, Microsoft Application Logs and Azure Active Directory Audit Logs by centrally saving and backing up log entries to Microsoft SQL Server, MySQL or SQLite.
- Use regular expressions and our Security Event Log parser to parse attribute value pairs to their native data types then save to your RDBMS for internal and external analysis (e.g. integer, decimal and date/time).
- Use our Log Entry Retention Policy Template to automatically delete old log entries no longer required for compliance.
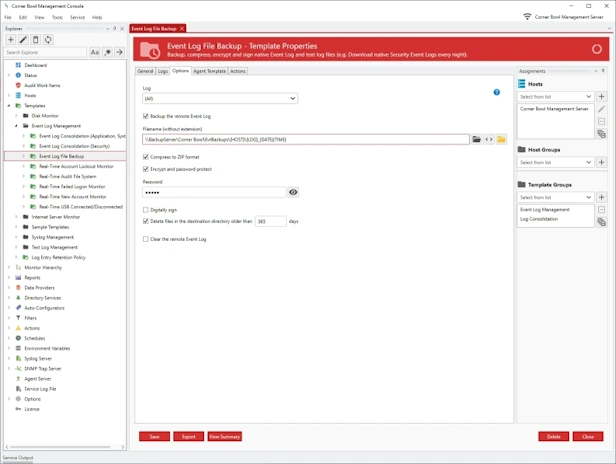
Event Log File Backup
- Centrally save, backup, zip, encrypt and digitally sign EVTX files in their native format.
- Use our Directory Cleaner Template to automatically delete old event log file backups no longer required for compliance.
- Batch Import and Audit Windows Event Log Files for CMMC and JSIG Compliance.
CMMC and NIST Compliance Software for the
DoD, MoD and Defense Contractors
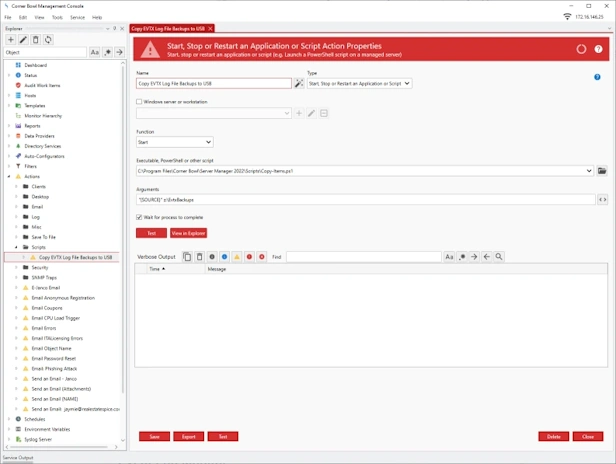
- Centrally save all EVTX files on air gapped networks.
- Manage small air gapped networks and stand-alone Windows workstations.
- Backup, compress and encrypt EVTX files using the FIPS compliant AES-256 encryption algorithm.
- Save EVTX files to USB devices.
- Run audit reports directly on stand-alone air gapped Windows workstations.
- Batch run audit reports for multiple stand-alone air gapped Windows workstations from external networks.
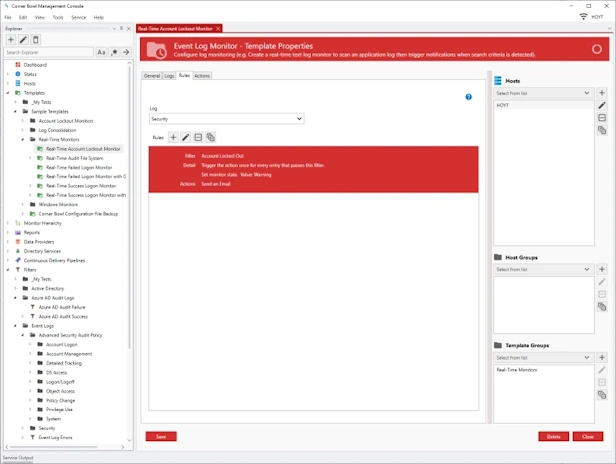
Event Log Monitor
- Real-time monitor Windows Event Logs and Microsoft Application Logs.
- Schedule monitor Azure Active Directory Audit Logs.
- Use regular expressions and our Security Event Log parser to parse attribute value pairs to their native data types for use in filters (e.g. integer, decimal and date/time).
- Create Complex Filter Criteria with support for any data type.
- Apply frequency rules (e.g. Get notified when any user fails to login 3 times within 5 minutes).
- Includes maintenance schedule rules.
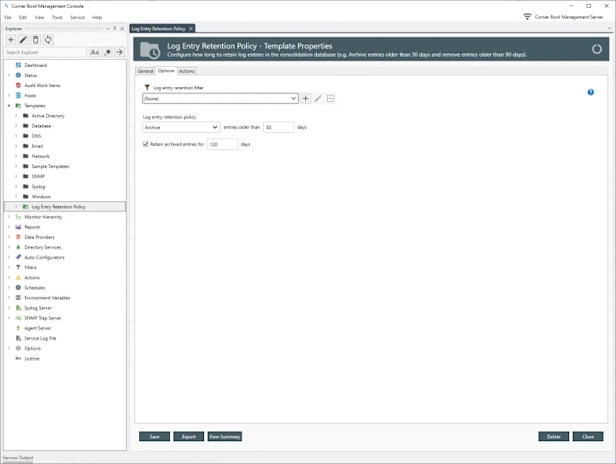
Event Log Entry Retention Policy
- Configure how long to retain event log entries in the log databases (e.g. Archive entries older than 30 days and remove entries older than 90 days).
- Schedule and manually remove event log entries no longer required for analysis and compliance.
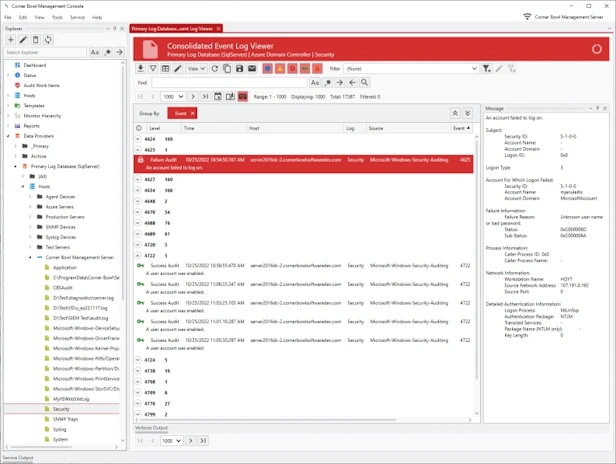
Event Log Analyzer
- Watch Windows Event Logs and Microsoft Application Logs in real-time.
- Page through large log files, search, highlight, view frequencies, mark entries and export result sets.
- Group and sort log entries using complex regular expression driven attribute value search criteria.
- Create complex filters from messages.
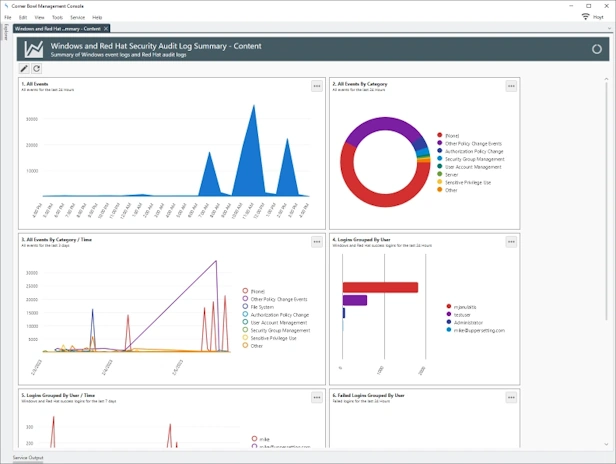
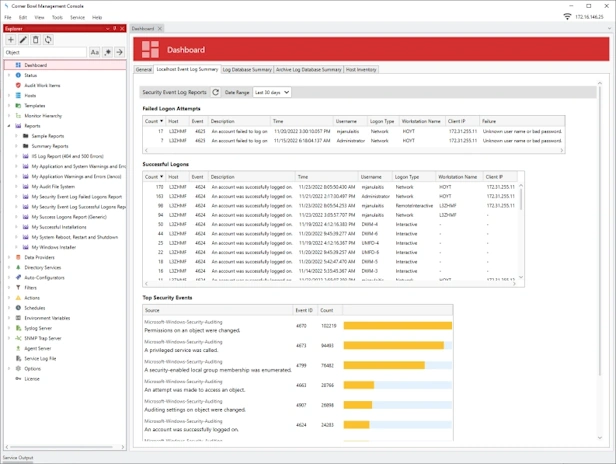
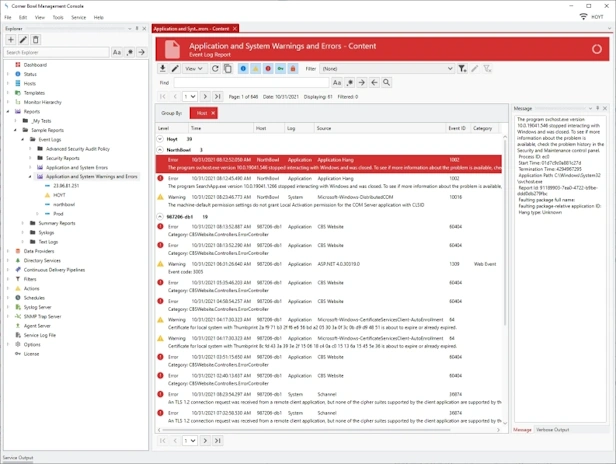
Security Event Log Compliance and Auditing Reports
- Includes 100+ Security Audit Policy Reports and Filters.
- Includes Critical Events Reports and Filters.
- Generate Azure Active Directory Audit, Sign-Ins and Identity Risk Log Reports.
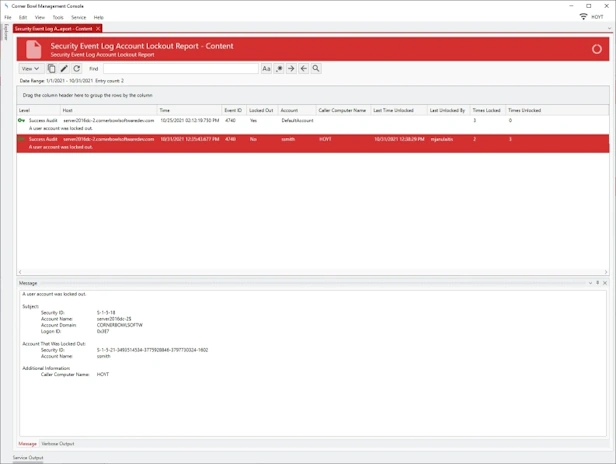
Account Lockout
- Audit Report that scans Active Directory and stand-alone servers for currently locked out accounts (e.g. Daily Lockouts).
- Audit Report that that searches consolidated Event Log entries and Event Log file backups for account lockout history events (e.g. Weekly Lockouts).
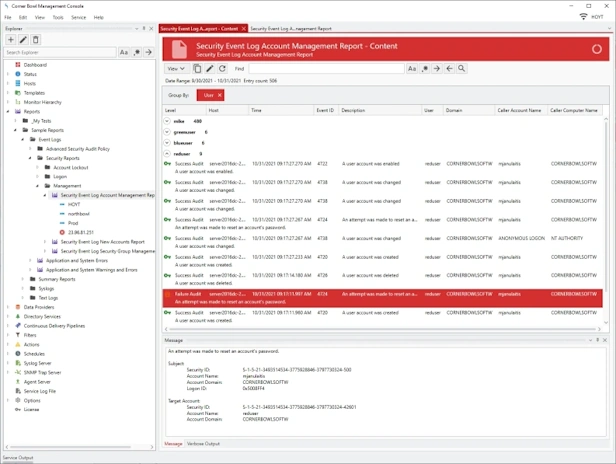
Account Management
Audit Report that searches consolidated Event Log entries and Event Log file backups for Account Management Security Event Log Events (e.g. Daily Account Management Events).
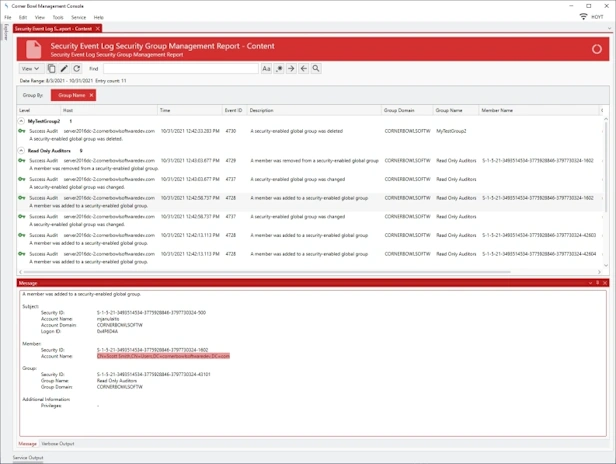
Online DocumentationSecurity Group Management
Audit Report that searches consolidated Event Log entries and Event Log file backups for Audit Security Group Management events (e.g. Daily Security Group Management Events).
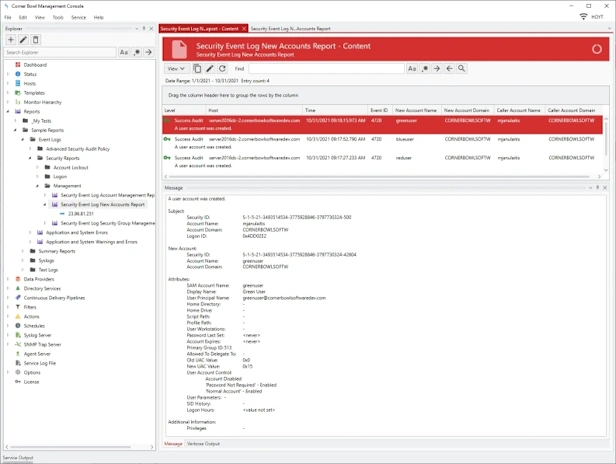
Online DocumentationNew Accounts
Audit Report that searches consolidated Event Log entries and Event Log file backups for Event ID 4720: A user account was created (e.g. Daily New Account Events).
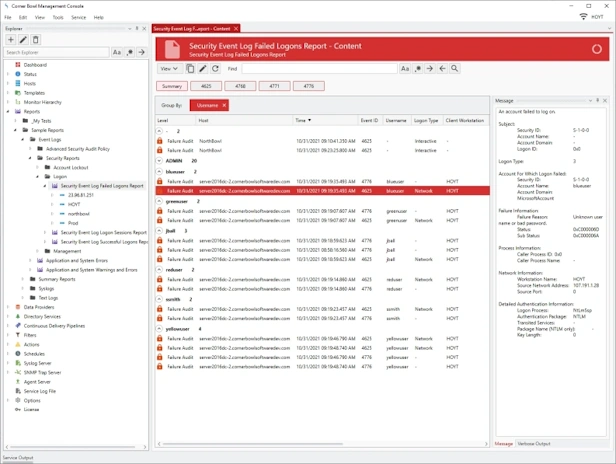
Online DocumentationFailed Logons
Audit Report that searches consolidated Event Log entries and Event Log file backups for failed logon attempts (e.g. Daily Failed Logon Events).
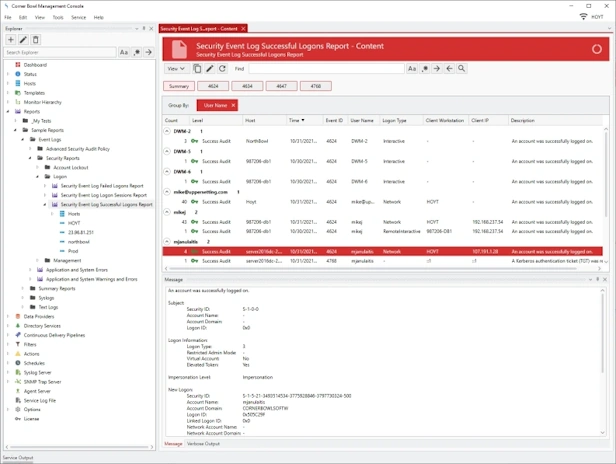
Online DocumentationSuccess Logons
Audit Report that searches consolidated Event Log entries and Event Log file backups for successful logons (e.g. Daily Successful Logon Events).
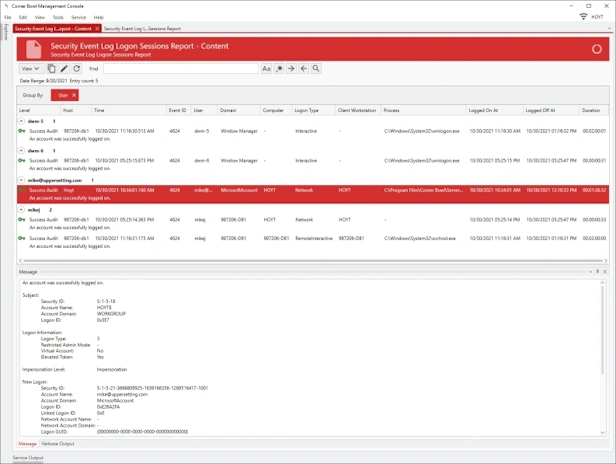
Online DocumentationLogon Sessions
Audit Report that searches consolidated Event Log entries and Event Log file backups for logon sessions (e.g. Daily Logon Sessions).
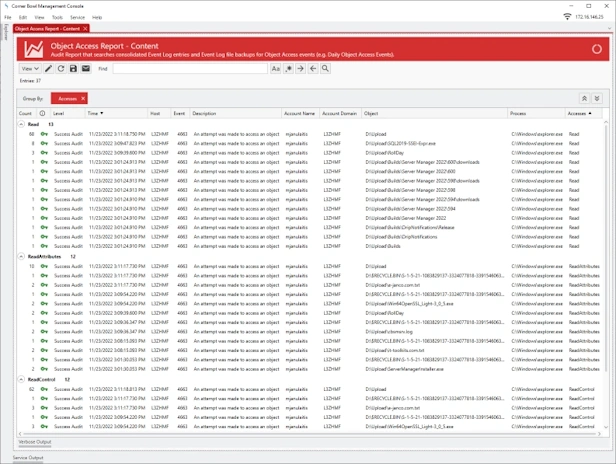
Online DocumentationObject Access
Audit Report that searches consolidated Event Log entries and Event Log file backups for Object Access events (e.g. Daily Object Access Events).
Online Documentation