How does Corner Bowl do it?
Baseline Scanning
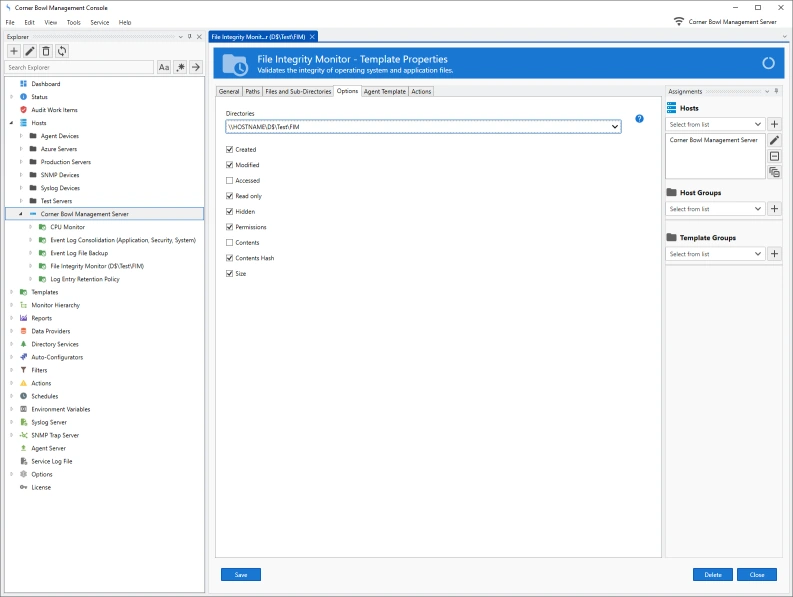
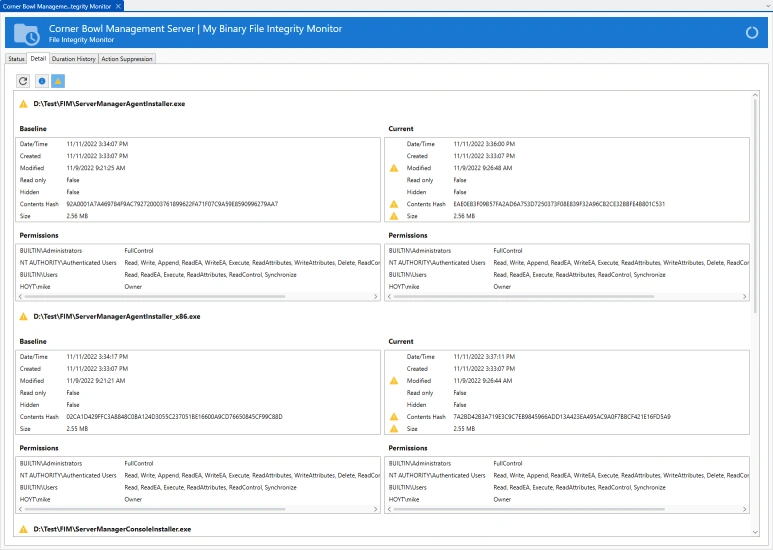
Corner Bowl Software's File Integrity Monitor scans directories using Windows Shares and SSH/SFTP to create file access, file attribute and file content baselines then continually re-scans to let you know when a file is accessed, modified or deleted. Access Permissions are scanned on Windows Servers using WMI.
Real-Time Object Access Auditing
If you want to know the user that modified a file on a Windows Server, enable Object Access Auditing on your Windows Server and you will get notified in real-time the instant a user accesses a file along with the IP address the access was made from. Please note, Object Access Auditing monitoring requires either a Server Manager or an Event Log Manager license.