What is Corner Bowl Directory Monitor?
Corner Bowl Directory Monitor is an extensive enterprise-class software monitoring and management tool for IT professionals that includes disk monitoring, directory monitoring, file integrity monitoring (FIM), ransomware detection, largest files and directories reporting, file access permissions reporting, proactive directory and temporary file cleaner, centralized file collection and more. Directory Monitor will help you fulfill compliance requirements for CJIS, CMMC, JSIG, NIST, GDPR, HIPAA, PCI/DSS and SOX.
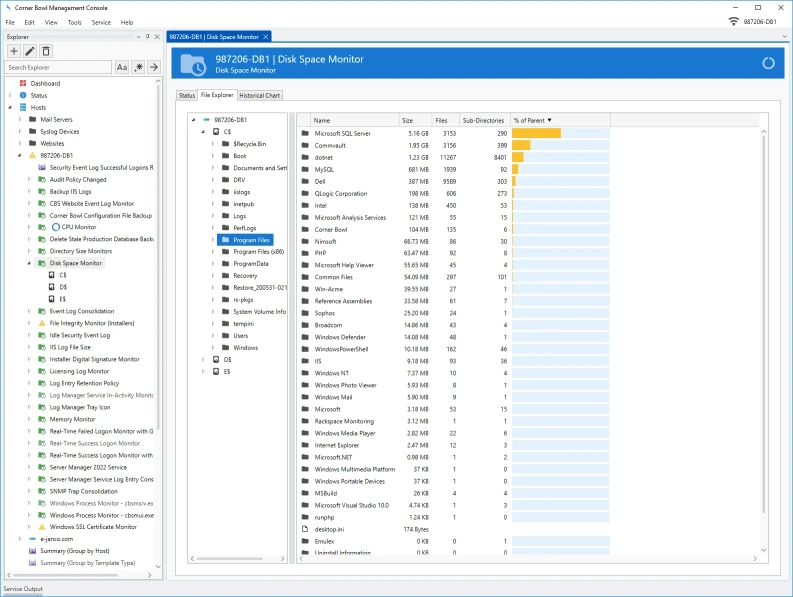
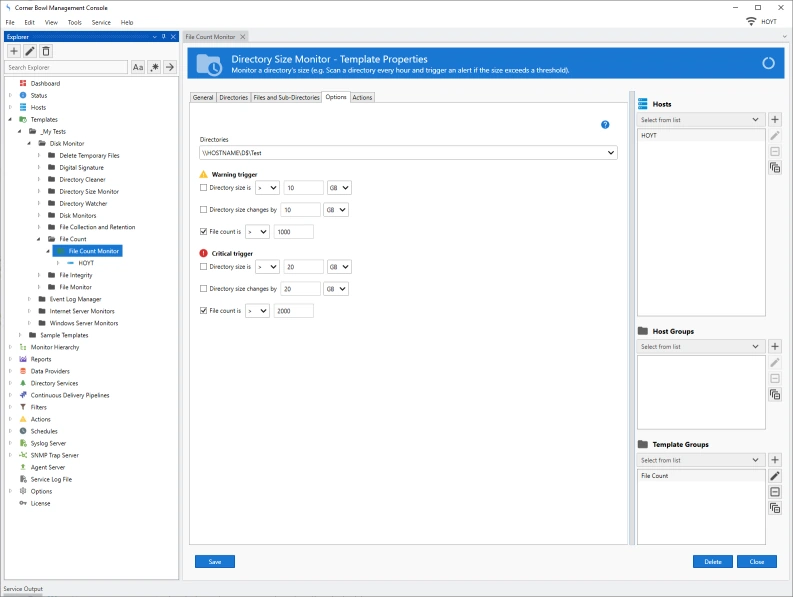
Directory Size Monitoring and Reporting
- Monitor directory sizes and change in directory sizes over time.
- View historical directory size charts.
- Interactively browse directory sizes and recursive delete sub-directories and files.
- Real-Time directory size monitor alerts include a list of the top largest files that caused the monitor to trigger.
- Summarize directory size information from all your servers to a single view.
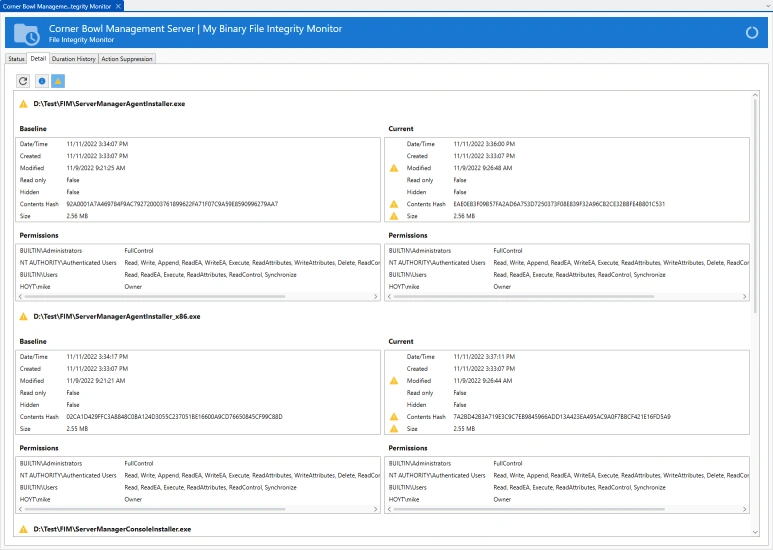
File Integrity Monitor (FIM)
Continuously monitor operating system, application and mission critical data files for user access, changes made to file content, attributes and access permissions on both Windows and Linux servers.
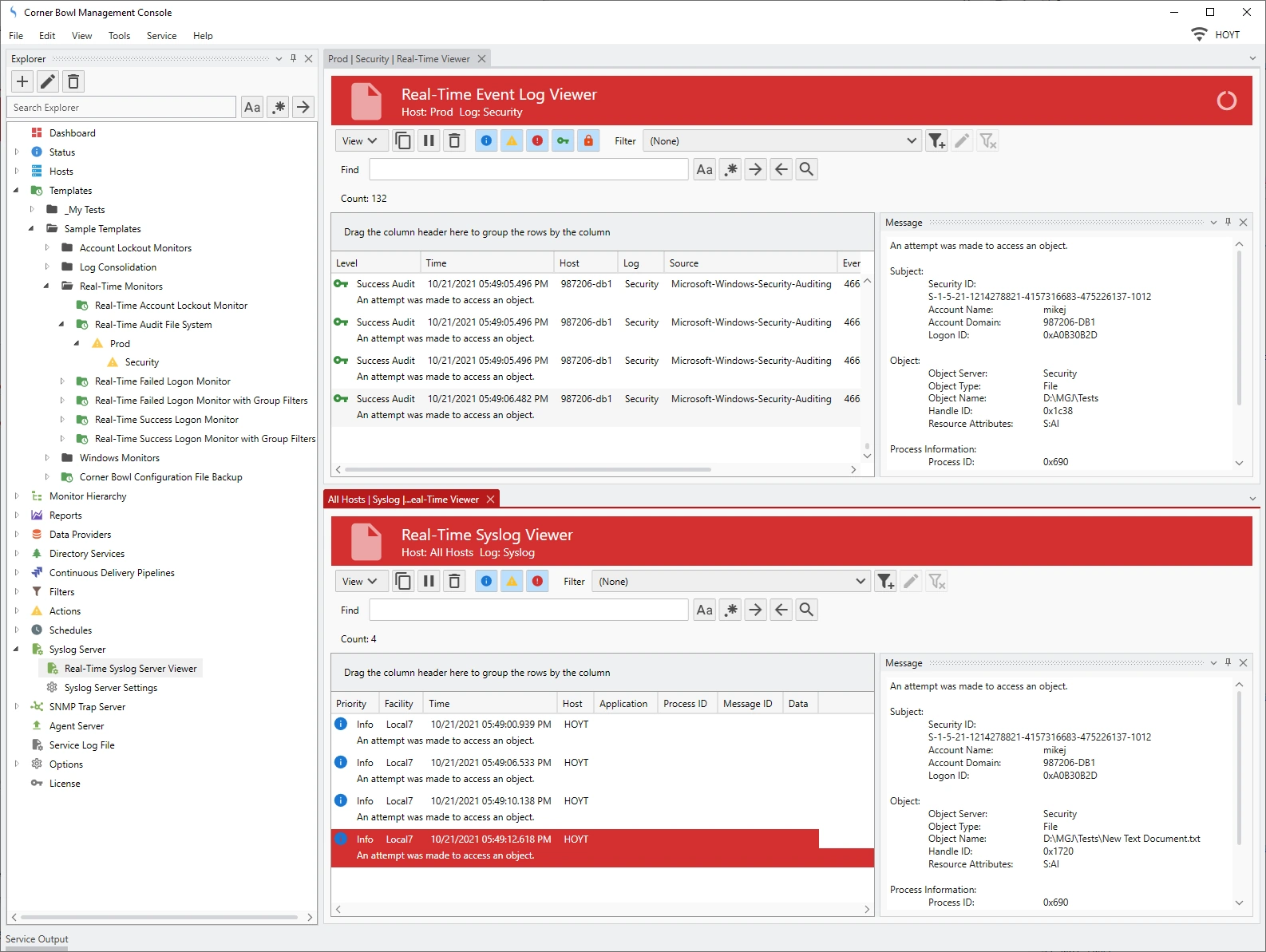
More Information | Online DocumentationRansomware Detection
Using a combination of FIM, real-time Object Access Auditing, and real-time directory monitoring, get notified the instant a file is modified, deleted, renamed, moved and created in any monitored directory or sub-directory on both Windows and Linux servers.
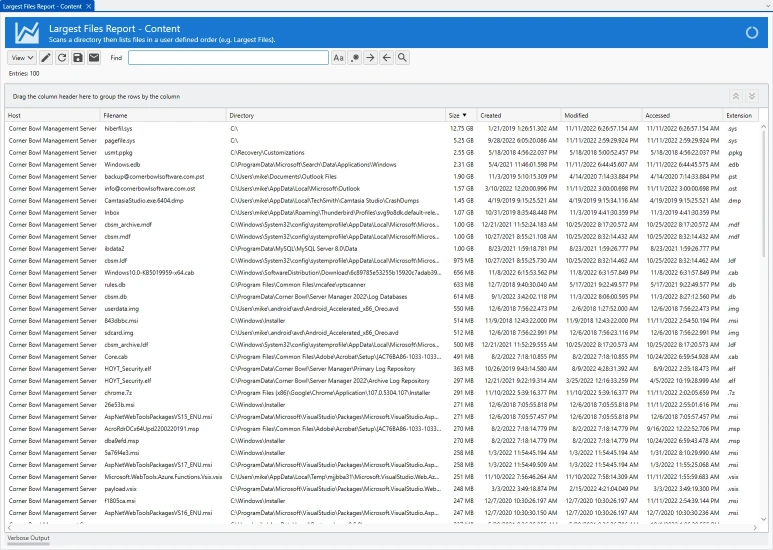
More InformationLargest Files Reports
- Run system wide largest files reports to see what files are consuming the most space.
- Configure the number of files and metadata columns to include in the report.
- Includes group and sort by options.
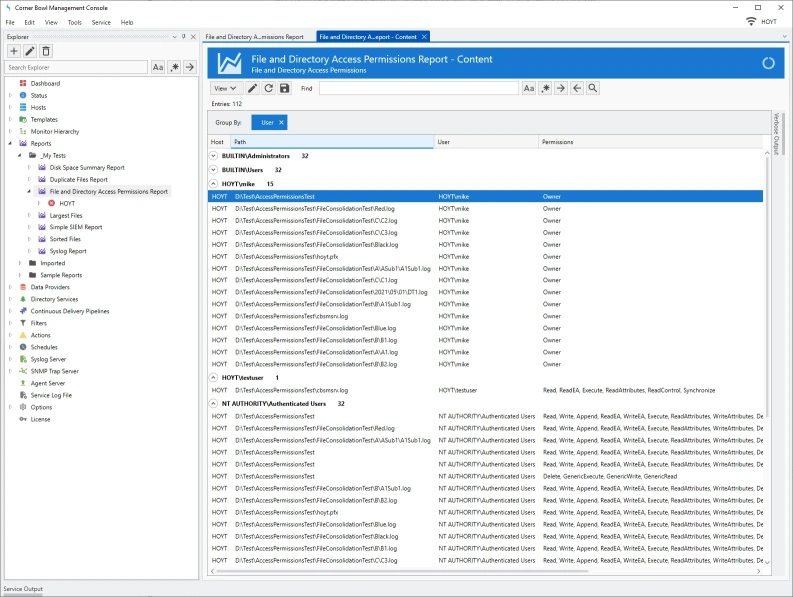
File and Directory Access Permissions Reports
- Recursively scan and report on all file and directory permissions.
- Configure search criteria including specific accounts and permissions.
- Define simple and detailed output rules.
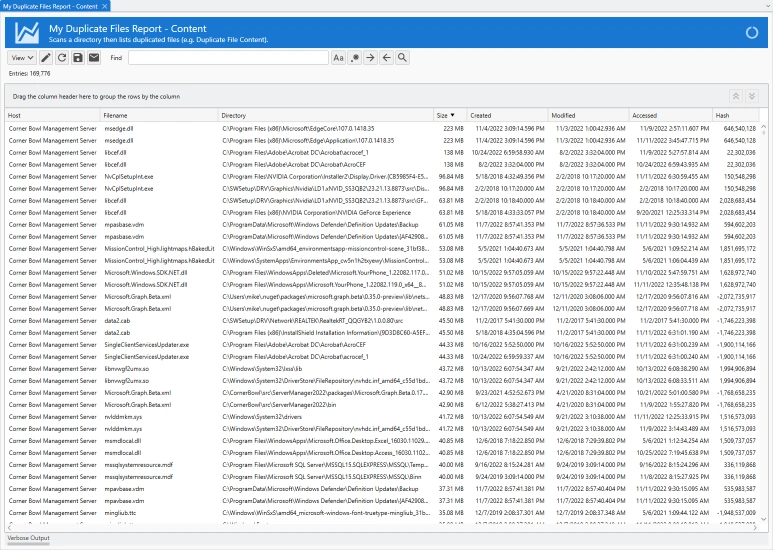
Duplicate Files Report
- Run system wide duplicate files reports to see what files can be deleted to free disk space.
- Define duplicate files using the following match options: Name, Size, Last Modified and Contents Hash.
- Includes group and sort by options.
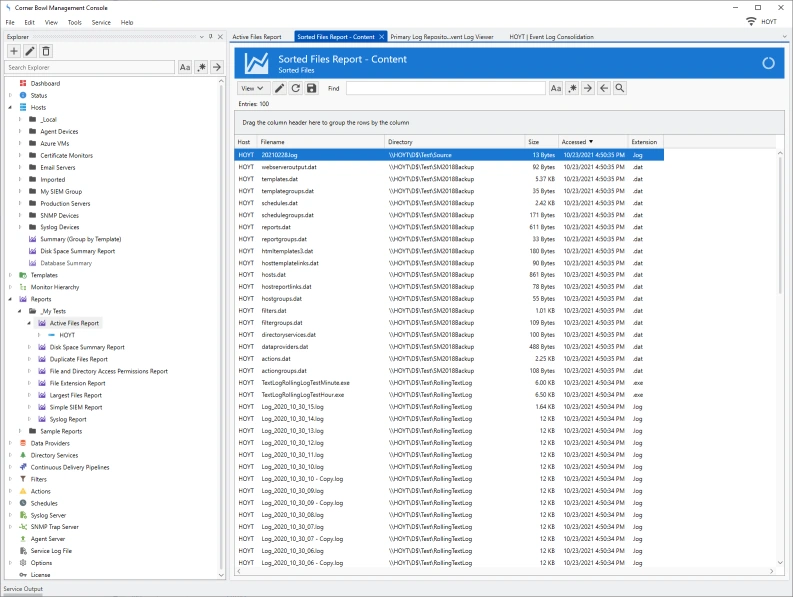
File Activity Reports
- Run system wide file activity reports to list files by most recently accessed or not accessed since a specific date, for example, receive a report that lists the top ten recently accessed files within a directory structure.
- Includes group and sort by options.
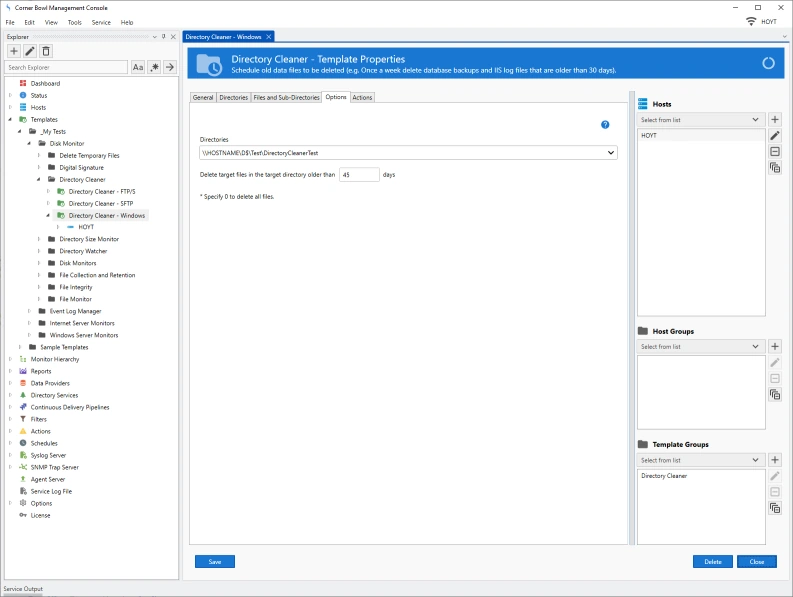
Directory Cleaner
- Automatically delete old database backups and log files on Windows and Linux servers.
- Schedule system and user temporary files to be deleted once a day.
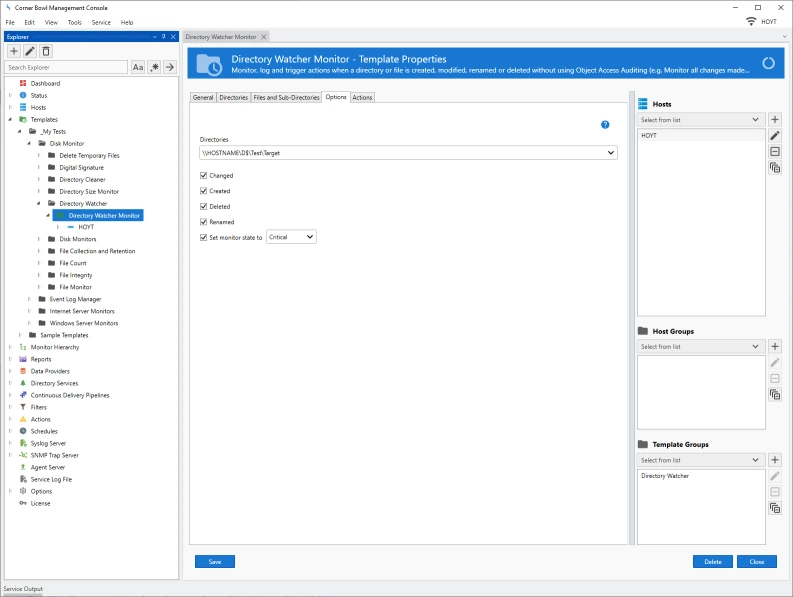
File and Directory Change Monitor
- Real-time monitor files and directories for created, modified, deleted and renamed events.
- Target results to a specific set of files using inclusion and exclusion search criteria, for example, log all changes to files with a .txt extension while excluding files named *_output.txt.
- Append results to a CSV file and send email notification alerts.
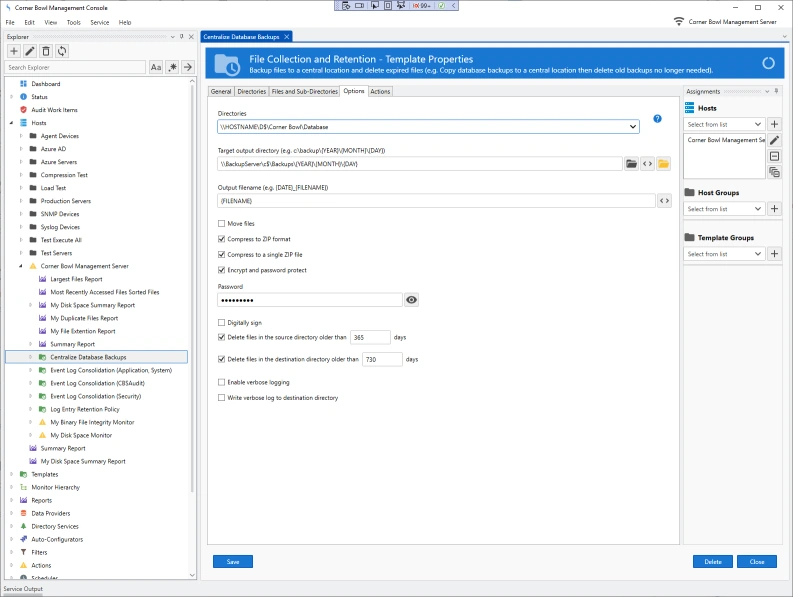
File Collection and Retention
- Continually backup files to a central location, for example, database backups and IIS log files.
- Deleted previously backed up files after they reach a certain age, for example 2 years.
- Start and restart services to unlock files.
File Count Monitor
- Monitor the number of files in a directory.
- Automatically run PowerShell Scripts to perform corrective actions, for example, shut down a service, delete unnecessary files then restart the previously shutdown service.